Security of consensus mechanisms is your trusty lock on the blockchain world’s vault door. Imagine a fortress so tight that not even the craftiest digital safecrackers stand a chance. That’s what we’re diving into. If you’re tired of jargon that makes your head spin, stick with me. We’re breaking down everything from hacker tricks to the solid walls that keep your crypto safe, and I mean brick-by-brick safe. Ready to become your own blockchain security guard? Let’s get to it and learn how to slam the door on those cyber-thieves for good!
Understanding Blockchain Consensus Mechanisms and Their Vulnerabilities
Exploring Proof of Work and Proof of Stake Security Concerns
Let’s dive right into the heart of blockchain, its security. It all starts with how blockchains agree, or reach a “consensus.” But here’s the kicker – these systems can have flaws.
Proof of Work, or PoW, is like a complex math problem. It’s safe, most of the time. Computers solve puzzles to add blocks to the blockchain. But, imagine if someone controlled most of the puzzle-solving power. They could twist the rules. We call this the 51% attack.
With Proof of Stake (PoS), on the other hand, it’s more about trust and less about power. Users lock up coins as a form of security deposit. Yet, it’s not perfect. Bad actors could still play the system if they hold a lot of coins.
Assessing the Risks of Distributed Ledger Attack Vectors
Next up – attack vectors. They’re the ways bad guys can attack a blockchain. There’s a bunch to watch out for. 51% attacks, where someone gets control of most of the blockchain power. It’s serious but can be stopped by keeping the network big and strong.
Then there’s Sybil attacks. They’re sneaky, where one user pretends to be many. The goal is to ruin the network’s trust. We stop these by checking identities closely.
Lastly, blockchain relies on puzzles called cryptographic hash functions. They keep our blocks strong and chained up nicely. And we use something called Byzantine Fault Tolerance (BFT) to keep the ship sailing smooth, even if someone tries to rock the boat.
So, in a nutshell, the safety of our decentralized networks comes down to being smart and staying one step ahead of those looking to do harm. We’ve got to keep checking and double-checking every piece of the system to make sure it’s as tough as nails. And never forget, being safe is a team sport in the world of blockchain.
Protecting Against the Most Common Attacks in Blockchain Systems
Strategies for Mitigating 51% and Sybil Attacks
Picture a fort. It’s solid and secure. Now, think of blockchain much the same. It’s like Fort Knox for digital info. But no fort is without its weak points. There are two big threats to blockchain: the 51% attack and the Sybil attack.
One threat is a 51% attack. It happens when someone controls more than half of the network’s mining power. They can block new transactions or even reverse ones they made. We fight this by keeping the network big and spread out. More miners mean no one person gets too much power.
Another nasty trick is the Sybil attack. Here, one person pretends to be many. They make fake identities to gain influence. To stop this, networks check who joins. They use things like testing a user’s computer power or holding a security deposit. These checks make it hard for a fake to slip through.
Remember, blockchain is a team game. To keep it safe, all players must follow the rules and stay alert.
Implications of Double Spending and Byzantine Fault Tolerance
Double spending is like spending a dollar twice. It’s a no-no in the blockchain world. This act can shake trust in digital currency. This is where Byzantine fault tolerance, or BFT, steps in. It’s the rulebook for nodes – the computers that make up the network – in situations where there is no clear enemy.
BFT’s job is simple yet vital. It ensures all nodes agree on a single version of truth, even if some nodes are up to no good. Think of it as a group of friends voting on what game to play. Even if one friend tries to cheat, the others can still decide on the game fairly.
With blockchain, this means a transaction only goes through when most nodes say ‘yes’. If a hacker tries to spend the same coin twice, the honest nodes won’t agree. So, the second transaction gets the red light.
In short, blockchain safety is a big deal. We keep a keen eye out for the sneaky attempts to break our trust. We build walls against attacks and set rules to keep everyone in line. It takes a lot of hard work, but it’s worth it. It keeps our digital Fort Knox locked tight.
Enhancing Blockchain Integrity with Advanced Security Measures
The Role of Cryptography in Safeguarding Consensus Algorithms
How does cryptography protect consensus mechanisms? Cryptography secures data through complex math. It makes sure only the right people can read and use it. Let’s get into the meat of it.
Consensus mechanisms make decisions in a blockchain. They agree on which blocks are valid. This stops cheaters and keeps the blockchain honest. But they can have weak spots. Bad actors might attack or mess with the consensus.
Enter cryptography. It’s like a superhero for blockchains. It mixes data into puzzles. Nobody can solve them without the right key. This means nobody can tamper with the data. It stays safe and sound.
“Cryptographic hash functions” are a big deal here. They turn data into short, unique strings of numbers and letters. Even a tiny change makes a totally different hash. So, anyone checking can spot fraud from miles away.
But why do we trust it? Because cryptography relies on math. Not luck, not chance—math. And math is tough to break. This is how we keep our consensus mechanisms as safe as possible.
Best Practices for Node Security and Digital Signature Reliability
What are the best ways to keep nodes safe? Keep nodes updated, use strong passwords, and limit access. Details matter, so let’s dive in.
Nodes are like the eyes and ears of blockchain. They watch over the chain and pass on info. Bad node security can lead to big trouble. It can let hackers in to cause chaos.
To lock the door tight, you use best practices. Keep your software updated. Outdated software has holes that hackers love. Like leaving your car unlocked with the keys in. You wouldn’t, right?
And passwords. Make them tough. Like puzzles you made as a kid, but crazy hard. This keeps the bad guys guessing.
Lastly, not everyone needs the keys to the kingdom. Limit who can touch your setup. Fewer people, fewer problems.
Now, onto digital signatures. They are your online handshakes. They prove you are you. They say, “Yes, this person is okay. They can go ahead.”
How do we make sure they are rock solid? Use strong cryptography again. And always check them. Twice, even. This means less chance for lies and tricks. We keep our blockchain world honest.
In all this, what matters most is keeping it simple. Clear rules, easy checks, and strong gates. We’re building fortresses, one block at a time.
And when you think about it, isn’t it cool? We are making something tough and safe. No fluff. Just solid blockchain goodness. We guard it, so it guards our data. Now that’s a treasure worth keeping safe.
Balancing Blockchain Immutability with Robust Security Protocols
Evaluating Block Verification Techniques to Prevent Ledger Tampering
Blockchains are like digital Fort Knoxes—super safe places to keep our valuable data. But just like the real Fort Knox, it is crucial to check for any weak spots that can let thieves in! Let’s zero in on block verification measures. They are key to keeping the bad guys away from our blockchain treasure.
Block verification is how we make sure each piece of data—which we call “blocks”—is real and unaltered. Think of it like the checks and balances that schools use when grading tests. First off, all data or operations on blockchain need a “yes” from certain members on the network. We call these members miners or validators. They work hard solving complex puzzles or holding digital coins as a stake to prove their honesty. This process is a big part of blockchains using Proof of Work (PoW) or Proof of Stake (PoS).
Alright, what’s the big deal with PoW threats and PoS weaknesses? Well, with PoW, imagine having to solve a big, big puzzle, and the first to finish gets a prize. It uses a lot of power and time. But it’s strong against cheating because redoing that puzzle is super hard. On the flip side, PoS asks participants to show they have a chunk of coins, and uses less power. The trick is making sure no one can use their coins to take over.
We keep our blockchain strong with something called Byzantine Fault Tolerance (BFT). It’s a fancy way of saying the blockchain can still work right, even if some parts are trying to mess things up. We use rules and math—like cryptographic hash functions—to lock down safety and stop people from acting sneaky.
Addressing Smart Contract Vulnerabilities through Rigorous Audits
Smart contracts are just rules written in code to handle transactions on the blockchain. They’re pretty smart, but not perfect. Sometimes there are flaws or loopholes that need fixing. These flaws can let hackers in, and we sure don’t want that.
So, how do we tighten up security? We need super careful checks—called smart contract audits. It’s like when teachers check your homework super closely to find mistakes. Experts go through every bit of the code to find any weak spots. They look for common mistakes or ways hackers might break in.
Auditing isn’t just a one-time thing, either. It has to happen often, because new ways of hacking can pop up, and smart contracts need to stay ahead of them. Remember the immutability versus security debate? It’s all about finding the right mix. We want our data set in stone, but not if it means we can’t fix a mistake or stop a thief.
In summary, keeping your blockchain safe is a big deal. By double-checking the miners or validators, and making sure smart contract rules are tight, we protect our info. It’s like making sure Fort Knox has thick walls and great guards, ready for anything bad that might happen. That’s how we stay safe and trust our fancy blockchain tech to handle our most important stuff.
We’ve walked through the key points of blockchain safety, from consensus methods to attack types. We’ve looked at common threats and how to stop them, like beating 51% and Sybil attacks, nixing double spending, and being smart about Byzantine faults. It’s clear that good cryptography and solid node rules are musts to keep consensus algorithms safe and make sure digital signatures hold up. Making sure every block in the chain checks out and putting smart contracts through tough checks are non-negotiable for keeping things tight and right.
In the end, it’s about striking the right balance. Yes, we want a blockchain that’s set in stone, but it has to be tough as nails too. It takes work, but with the right steps, blockchain can stay solid and secure. Follow these practices, and we can trust in blockchain’s promise, with fewer bumps in the road. Stay sharp and keep your blockchain guarded!
Q&A :
How do consensus mechanisms ensure the security of a blockchain?
Consensus mechanisms are crucial for validating transactions and maintaining the integrity and security of a blockchain. They work by requiring network participants (nodes) to agree on the validity of transactions before they are added to the blockchain. This prevents fraud and double-spending by making it extremely difficult for a bad actor to manipulate the ledger, as it would require overwhelming consensus from the network.
What are the potential vulnerabilities in consensus mechanisms?
While consensus mechanisms are designed to provide security, they are not immune to vulnerabilities. Potential weaknesses include the risk of a 51% attack (particularly in Proof of Work systems), where if an entity gains majority control of the mining power, they could potentially alter the ledger. Other vulnerabilities include Sybil attacks, in which a user creates multiple fake identities to gain undue influence in the network, and various other forms of potential collusion among participants.
How do different consensus mechanisms compare in terms of security?
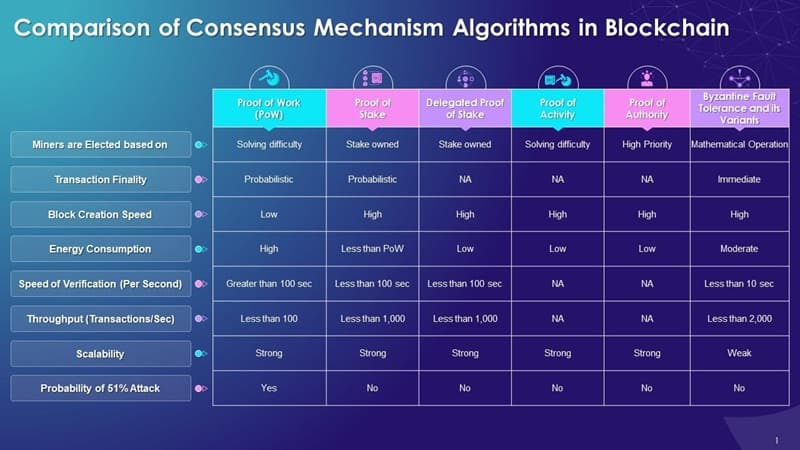
Different consensus mechanisms offer varying levels of security based on their resistance to certain types of attacks, energy consumption, and decentralization. For instance, Proof of Work (PoW) is known for high security but also high energy consumption, while Proof of Stake (PoS) offers a more energy-efficient alternative but may be more susceptible to concentration of power issues. Delegated Proof of Stake (DPoS), Practical Byzantine Fault Tolerance (PBFT), and other mechanisms also present a trade-off between efficiency, scalability, and security.
Can quantum computing threaten the security of consensus mechanisms?
Yes, quantum computing presents a theoretical threat to consensus mechanisms, especially those based on cryptographic functions that could be broken by quantum algorithms. In particular, mechanisms using cryptographic signatures could become vulnerable if quantum computers are able to break these signatures. The blockchain community is actively researching post-quantum cryptography and other strategies to mitigate these potential risks.
What improvements and innovations are currently being explored to enhance the security of consensus mechanisms?
Blockchain developers and researchers are looking into several improvements and innovations aimed at enhancing the security of consensus mechanisms. These include developing more robust cryptographic protocols, exploring new consensus algorithms that reduce vulnerability to attacks, implementing sharding techniques to increase scalability while preserving security, and applying formal verification to ensure correctness of the underlying protocols. Additionally, layer two solutions and cross-chain interoperability features are being developed to bolster security and alleviate certain stress points in existing consensus models.

RELATED POSTS
Challenges That May Hinder Blockchain Adoption: Adoption Really at Risk?
"Challenges that may hinder blockchain...
Major airdrop – Easy wealth with Major Tokens
Looking for a game that...
Challenges of Blockchain in Healthcare: Revolution or Roadblock?
Navigating data security and patient...
What is Data Tokenization? – The Key to Secure Data Management
What is Data Tokenization? This...
Naoris Protocol Airdrop: Get free NAORIS Tokens
Naoris Protocol is an advanced...
Forgotten Runiverse: A promising NFT Game on Ronin Network
Forgotten Runiverse is emerging as...
Quantum-resistant cryptography for blockchain
Protect Your Blockchain with Quantum-Resistant...
How Blockchain Boosts Educational Equity: A Tech Revolution in Learning
How can blockchain promote educational...
Yala Airdrop – A Great Opportunity to Earn Free Tokens Today
Discover Yala Airdrop now –...
Can Blockchain Revolutionize Voting? Unpacking Fraud Prevention Potential
Can blockchain prevent voter fraud?...
Future Applications of Blockchain Technology: Beyond Bitcoin to Bold Innovations
Future applications of blockchain technology:...
What are the three advantages of using blockchain technology
Curious about “What are the...
Blackwing Airdrop – HOT Opportunity to Receive Tokens from BXP
In the fast-moving cryptocurrency space,...
Unraveling the Mystery: Cryptocurrency vs. Blockchain Demystified
Understanding the Difference: Cryptocurrency vs....
Unlocking Tomorrow: Examples of future applications of blockchain
Examples of future applications of...
Blockchain Prediction Market: Navigate the Future, Bet on Outcomes
Blockchain Prediction Market: Explore Decentralized...