Imagine this: one person with many masks, each pretending to be a unique user on a network. This is a What is a Sybil attack on blockchain; a trickster’s haven where a single entity creates multiple fake identities to gain undue influence and disrupt the digital ledger’s democracy. It’s a pressing issue that puts blockchain’s security to the test as it exploits its key vulnerability: trust. You might think that blockchain is invincible, but without proper defenses, it can fall prey to cleverly disguised sabotage. This blog reveals the hard truths about Sybil attacks and guides you through understanding and guarding against this digital deception.
Demystifying the Basics: Understanding Sybil Attack Fundamentals
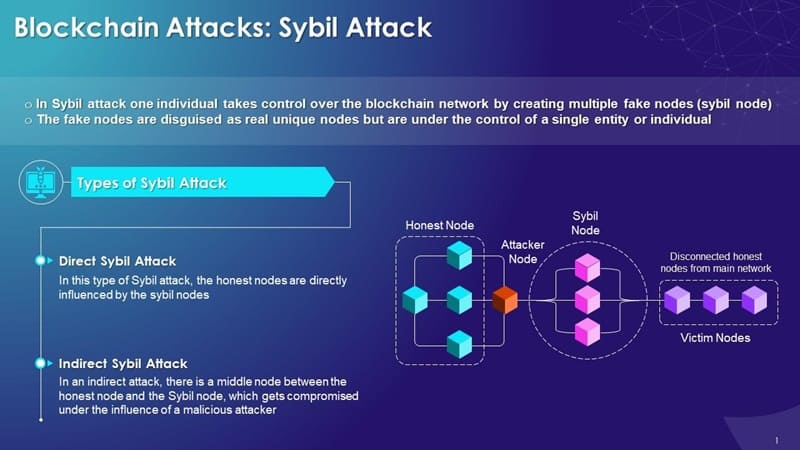
Dissecting the Definition: What constitutes a Sybil Attack?
A Sybil attack is when a user fakes many identities in a network. This hurts the trust in the network. In blockchains, it can mess with consensus, or agreement, by making it seem like more nodes back certain actions. This is a big deal for blockchains, which rely on many different nodes or users to agree on what’s true or should happen, like confirming a cryptocurrency transaction. Fake identities on networks are like wolves in sheep’s clothing, aiming to fool the system for personal gain.
Sybil attacks can pretend to be many nodes, which endangers the integrity of peer-to-peer networks. Decentralized networks are more open to attacks because they often allow unknown nodes to join. Attackers create lots of fake nodes to gain a large influence in the network. They might disrupt the operation of the blockchain, trick the network into accepting false transactions, or stop real transactions from happening.
Let’s look at a quick Sybil attack example. Think of a neighborhood watch program where each house is a node on a blockchain. If one person pretends to be many different houses, they could sway decisions unfair.
Highlighting the Risks: How Sybil Attacks Exploit Blockchain Vulnerability
Sybil attacks punch right at cryptocurrency security threats. They make fake identities and trick the blockchain into thinking something is right when it’s not. This can lead to wrong transactions or bad actors getting more control than they should.
Blockchain consensus mechanisms, like proof of work or proof of stake, have built-in ways to fight off these attacks. Proof of work makes attackers do hard math problems to earn the right to add new transactions. It costs a lot, so it’s hard for one person to control too much. Proof of stake, on the other hand, lets those with more currency have a bigger say. This also makes it costly to attack. Still, Sybil attacks can sneak through if not checked.
Network security in blockchain matters a lot. We need Sybil-resistant algorithms and careful node checks to keep our cryptocurrency safe. Think of it like having a good lock on your door. It keeps the bad folks out. Protecting digital identity is also a must. By making sure everyone is who they say they are, we help keep the network true. Identity validation techniques are like the bouncer at the door, checking IDs.
The key is to stop Sybil attacks before they start. We need good Sybil attack detection methods and solid prevention plans. It’s like having a neighborhood watch with binoculars, always looking out for trouble. Luckily, smart folks work on combatting Sybil attacks in blockchain daily. They ensure that when you trade your cryptocurrency, you can trust it’s safe and sound.
But why should you care? Simple. If attacks mess up the blockchain, it can affect your money and trust in the technology. Understanding blockchain security helps us all to spot and stop these sneaky attacks together.
The Battle for Security: Defending Against Deceptive Identities
Strengthening Defenses: Developing Sybil-Resistant Algorithms
In blockchain, we must always be on guard. Fake identities are like wolves in sheep’s clothing. They blend in, hoping to harm the trust we have in our networks. This is the core of a Sybil attack. It’s when one user pretends to be many. They do this to gain power in the network. We call these fakes “Sybil nodes.”
Picture a room where everyone must vote, but one person holds many masks, posing as different people. If they vote many times, the result isn’t fair. That’s what happens during a Sybil attack on blockchain. To stop this, I work on special codes called Sybil-resistant algorithms. They help ensure everyone is who they say they are.
These algorithms are vital for cryptocurrency security. Without them, multiple nodes could control a network. This would be bad for everyone’s digital cash. We make these defenses stronger to keep our virtual money safe.
Enhancing Verification: Advanced Identity Validation Techniques
Identity checks are also a key part of the battle. We use tough to guess questions and checks to prove who is real. This is hard to do without giving away private details, but it’s crucial.
We call this “node verification.” Each user, or node, gets checked without revealing who they really are. This way, we protect their secret identity while making sure they’re not a bad actor.
To fight Sybil attacks, we keep improving how we check identities. We create new ways to find out who might be lying about who they are. Doing this stops one user from having too much say. It keeps the peer-to-peer spirit of blockchain alive and well.
These checks are a bit like a digital ID card. But instead of a name or a face, we look at how they behave and connect. If a user acts oddly, the system might flag them.
To sum up, we’re in a fight to keep blockchain safe. We’re always coming up with new codes and checks to keep our guard up. It’s like building a digital castle with high walls and smart guards to keep the invaders out. It’s a tough battle, but one we’re suited to win.
Consensus Under Siege: Assessing Mechanisms’ Sybil Resistance
Comparing Proof of Work and Proof of Stake: Vulnerabilities and Strengths
Proof of work keeps blockchain safe by making users solve hard puzzles. This hard work stops fake users from taking over because they would need a lot of computer power to solve the puzzles. Those puzzles use a lot of energy. That’s a big problem we need to fix.
On the other hand, proof of stake gives control based on how much cryptocurrency you own. But if someone owns a lot, they might have too much power. This could make the system unfair. We call this the “nothing-at-stake” problem. People can vote for different blocks without risk which can lead to fake chains.
Is one better than the other? Proof of work has been stronger against Sybil attacks so far. But it has that big energy problem. Proof of stake is new and uses less power. But it could give too much power to the rich. We are working hard to make proof of stake safer from these attacks.
Byzantine Fault Tolerance and its Role in Thwarting Deception
Now let’s talk about Byzantine Fault Tolerance or BFT. It’s named after a problem where army generals couldn’t trust each other’s messages. In blockchain, BFT helps networks agree on things, even if some users can’t be trusted.
BFT is a big help in fighting deception. It cuts down the chance that liars can hurt the network. If some nodes are bad, BFT makes sure they can’t trick the whole network. It’s like having a group of trusted friends check if what you hear is true. We use BFT to stop Sybil attacks by catching liars before they cause trouble.
To fight Sybil attacks, we must check who is joining the network. We can’t let too many fake users in. It’s like having a door guard who checks IDs. But we have to be smarter than the attackers. They know all the usual tricks. That’s why I work on Sybil attack detection every day. We must think like the attackers to stay ahead.
Blockchain is amazing but not perfect. Bad guys always look for ways in. They use Sybil attacks to try and take control. But we’re on the watch. We build walls like proof of work and proof of stake. And we have lookouts like Byzantine Fault Tolerance.
Remember, staying safe is a team job. We all have to help. Use strong passwords. Be careful online. If we all do our part, we can keep blockchain safe and fair for everyone.
Preventing Digital Deceit: Strategies for Sybil Attack Mitigation
Deployment of Sybil Attack Detection Systems
Keep your blockchain safe is tricky, but not impossible. Picture this: a carnival game where you spot the fakes among genuine prizes. This is like finding fake identities in a blockchain. These fakes, or Sybil attacks, can hurt cryptocurrency security and trust. How do we spot them? With smart detection systems.
These systems look at how nodes behave. Nodes are like the carnival’s game booths. If a booth seems odd, it might be a fake (a Sybil node). The system checks if a node acts differently from the rest. Does it make too many connections too fast? If yes, it could be trying to take control. We also bring network security experts, like me, who use their skills to outwit attackers. We are like the savvy players who know every trick and tell the fakes from the reals.
Implementing Comprehensive Prevention Methods: Network Robustness and Ethical Hacking Practices
Now, let’s beef up our defense. One way to do that is by improving our network “muscle” – its robustness. We do this with special Sybil-resistant algorithms. Think of it like a carnival game that’s tough to cheat at. We make it hard for one person (or Sybil attacker) to play all the games (or control the network).
Next, we embrace ethical hacking. Here, the good guys think like the bad guys to find weak spots. Like a pro player who checks every part of the carnival game for a secret flaw, ethical hackers look for blockchain weak spots. This means we sharpen our tools before attackers do. We also teach the blockchain to defend itself, learning from each attack.
For a blockchain to stand strong, every node (game booth) must be checked. Verified nodes help keep peer-to-peer network integrity in top shape. Think of it like a fair where all games are tested for fairness. No sneaky tricks allowed!
By combining detection systems, ethical hacking, and solid network design, we stay one step ahead. Just like carnival champs keep winning stuffed animals, we keep winning the fight against Sybil attacks. This way, we make sure that the blockchain stays like a fun and fair carnival for everyone.
In this post, we dived deep into Sybil attacks, starting with the basics. We discovered how they threaten blockchain tech and the risks they pose. Then, we explored how to shield our digital spaces with Sybil-resistant algorithms and better identity checks.
We examined different defense mechanisms, comparing Proof of Work to Proof of Stake, and how Byzantine Fault Tolerance can be a game-changer in this fight. Lastly, we learned that putting strong detection systems in place and adopting thorough prevention strategies can keep our networks secure.
I hope you now feel more informed about Sybil attacks and the power of robust defense tactics. It’s essential for our digital safety, and with the right know-how, we can help prevent these tricky attacks. Stay aware, stay secure!
Q&A :
What Exactly Is a Sybil Attack in the Context of Blockchain?
A Sybil attack on the blockchain is a security breach where a single entity creates many fake identities to gain a disproportionate amount of influence on the network. These multiple identities, often called Sybil nodes, can subvert the network’s reputation system, which is critical in peer-to-peer environments that rely on the assumption that each user holds only one identity. In blockchain, this kind of attack threatens decentralized consensus mechanisms, potentially allowing a malicious actor to disrupt transactions and undermine the integrity of the ledger.
How Can a Sybil Attack Affect a Blockchain Network?
A Sybil attack can significantly affect a blockchain network by undermining trust among users. An attacker could compromise consensus mechanisms, which are vital for validating transactions and keeping the ledger accurate and reliable. The network becomes vulnerable to double-spending, where the same digital asset is spent more than once. Furthermore, an effective Sybil attack might hinder the normal operations by slowing down transaction validations or causing network congestion.
What Measures Can Prevent Sybil Attacks on Blockchain?
Blockchain networks can employ several strategies to prevent Sybil attacks. The most common method is using a Proof of Work (PoW) or Proof of Stake (PoS) mechanism, which makes it cost-prohibitive to control a majority of identities on the network. Additional measures include requiring nodes to stake currency as collateral, implementing strong authentication protocols for nodes, and using network analysis to detect and isolate suspicious activity.
Are There Any Notable Incidents of Sybil Attacks on Blockchain?
While specific Sybil attacks on blockchain aren’t frequently publicized due to the robust security measures taken by blockchain platforms, there have been instances in both blockchain and other P2P networks. The nature of blockchain often makes successful Sybil attacks difficult, but potential incidents and vulnerabilities are commonly explored and addressed by the crypto community to enhance security proactively. Historical P2P network incidents outside of blockchain serve as cautionary tales and learning points for securing decentralized networks.
Is Bitcoin Susceptible to Sybil Attacks?
Bitcoin, like any decentralized network, is theoretically susceptible to Sybil attacks. However, its use of the Proof of Work (PoW) consensus mechanism helps protect it against such threats. The high computational power required to solve the cryptographic puzzles and add a block to the chain acts as a deterrent to would-be attackers. Nonetheless, network vigilance is crucial as attackers continuously evolve their strategies, which is why the Bitcoin community remains proactive in implementing security measures and updating protocols.


RELATED POSTS
Unraveling the Mystery: Cryptocurrency vs. Blockchain Demystified
Understanding the Difference: Cryptocurrency vs....
Comparative DAG vs Blockchain: Decoding the Future of Tech Networks
Compare the Structural Differences: DAG...
Blockchain Brilliance: How Students Can Master Their Data Management
Role of students in managing...
Pebonk Kombat – The next frontier in gaming and crypto
Pebonk Kombat is revolutionizing gaming...
What is blockchain technology in simple terms for beginner
What is blockchain technology in...
History of Blockchain: The Revolutionary Timeline That Changed Tech Forever
"Explore the Genesis of Blockchain,...
Overview of Andrew Tate’s crypto wallet
Uncover the secrets of Andrew...
Peaq Crypto: A disruptive Blockchain platform
Peaq Crypto, a high-performance layer...
What is Tokenized Real Estate? – Unlocking Global Investment Opportunities
What Is Tokenized Real Estate?...
Consensus Algorithms Unveiled: Securing the Digital Frontier
Understanding Consensus Algorithms in Blockchain...
Enterprise Blockchain Emergence: Unlocking Top Security Requirements
Addressing specifics of #blockchain model...
What can you get with leetcoins? Discover now!
What can you get with...
Blockchain Security Audits: Essential Shields Against Cyber Threats
Understanding the Importance of Blockchain...
Vessel Finance: The DEX with near-zero gas fees
In the ever-evolving world of...
How to Participate in the Avail Airdrop and Earn $AVAIL Tokens Breakthrough
Avail Airdrop offers a simple...
Blockchain Revolution: How Is Blockchain Used In Different Industries
How is blockchain revolutionizing finance,...