Routing attacks on blockchain networks are the silent predators waiting to pounce on your crypto assets. Think of blockchain like your digital Fort Knox. It’s supposed to be unbreakable, right? Wrong. Here’s the harsh truth: your digital gold is at risk if you don’t know the ins and outs of blockchain security. With crafty enemies always digging tunnels beneath your defenses, understanding how these attacks strike is your first line of defense. Buckle up as we delve into the belly of the beast—where a small chink in your blockchain armor could mean disaster. Let’s armor up and build an impenetrable fortress together.
Understanding the Threat: How Routing Attacks Compromise Blockchain Security
Types of Routing Attacks on Blockchain
You know blockchain security is a big deal. It’s like keeping your treasures safe in a digital Fort Knox. But just like a real fort has many doors, a blockchain network has many points where bad guys can enter. They use tricks called routing attacks to sneak in. Let’s talk about these tricks.
Sybil attacks happen when one bad guy pretends to be many users. Think of it like one person wearing lots of masks to a party. This confuses the network. It’s hard for the network to trust new friends.
Eclipse attacks are sneaky. They cut off a node, or a user, from its real network buddies. It’s like being trapped in a room with fake friends. The node can’t get the info it needs to make smart choices.
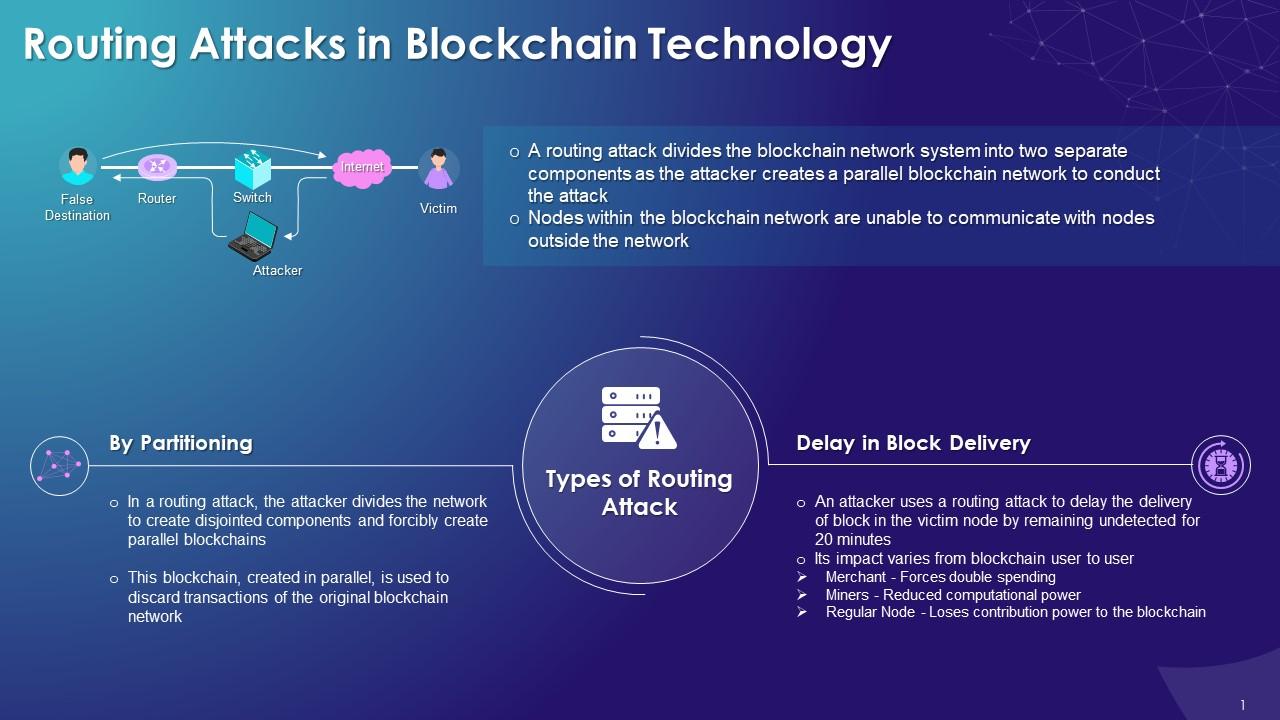
In a BGP hijacking, the bad guy redirects the internet path. It’s like switching road signs so the data takes a wrong turn and ends up where it shouldn’t.
These sneaky moves mess with the trust and flow of data. They make it hard for blockchain to do its job right.
The Impact of Routing Disruption on Blockchain Operations
When routing goes wrong, it’s not just annoying—it’s harmful. Here’s why.
It can slow down or stop deals you want to make. This can cost you time and money.
It can let bad guys see private info they shouldn’t. Imagine someone reading your diary—that’s not good!
It can give bad guys a chance to trick the system. They can make fake deals or block real ones. This hurts everyone’s trust in blockchain.
We need to be smart and stop these attacks. We do this by checking our blockchain for weak spots and fixing them with cool tech moves. It’s like having guards who are always watching out for trouble.
We also help blockchains talk to each other better. This makes it harder for bad guys to trick them. It’s like teaching your treasure vault to yell “Help!” when someone it doesn’t trust comes close.
So now you see, keeping blockchain safe is a big job, but we can do it by being smart and ready to act. It’s all about protecting your digital gold in this wild world of the internet.
Proactive Defense: Strategies to Secure Decentralized Ledgers
Network-Layer Attack Prevention in Cryptocurrency
When you keep your money in a bank, you trust it’s safe. Blockchain is like your digital bank. Just like a real one, it can get attacked. These attacks are crafty and happen in the network itself. When bad players mess with blockchain’s network, it’s called a ‘routing attack’. They trick the system, so messages go to the wrong place. This is bad news for trust and safety.
What’s key to stopping these network-layer attacks?
Quick answer: rock-solid planning and smart tech.
Long answer: preventing network-layer attacks in cryptocurrency means we must always be steps ahead of the bad guys. We use our know-how to stop them cold. Our tech has to check messages and spot lies. It has to tell us if something fishy is going on. If it does, we act fast to block the attack.
Implementing Secure Routing Protocols for Resilience
Think of routing protocols like maps for digital data. They tell info where to go on the internet. The right map keeps our blockchain safe from wrong turns. A secure map stops attackers from leading our data astray. We call this map a ‘secure routing protocol’.
How do secure routing protocols shield us from harm?
Quick answer: they give us a plan for data to follow that attackers can’t mess with.
Long answer: deploying secure routing protocols is like building a wall around our digital city. They make sure messages take a safe path. They bounce off any fake signs hackers put up. These protocols are our knights in shining armor. They guard our peer-to-peer network and keep our ledger from getting split up by sneaky tricks.
In short, we’ve got to keep our blockchain fortress tough. Each ledger is a brick in our wall. Secure routing protocols are the mortar. Staying proactive is the best defense. We always have to think ten steps ahead. We improve security and trust, one block at a time.
Cryptographic Shielding: Enhancing Transaction Security
Mitigation Techniques for Preventing Blockchain Partitioning Attacks
Blockchain is like a digital Fort Knox. But unlike Fort Knox, it’s not just gold we’re securing – it’s data. Lots of it. A partitioning attack can split a blockchain, keeping parts of it from talking to each other. Bad news, right? It’s kind of like taking a sledgehammer to the fort’s wall. But don’t worry. We’ve got some solid tricks to stop these attacks.
First up, we must get smart about our network layout. If a network’s setup is all over the place, it’s easy pickings for bad actors. Think of it like a game of whack-a-mole — you’ve got to be ready at all spots. By keeping an eye on the network, we can spot dangers and shut them down fast.
Next, enter encryption. This is our cryptographic shield. When data zips around the blockchain, encryption keeps it safe. It scrambles the data so well, if hackers grabbed it, they’d get gobbledygook. Picture a secret code that only you and your buddy know. That’s encryption for you.
Also, have you heard of consensus protocols? They’re critical. They make sure that all the parts of a blockchain agree before new blocks get added. It’s like getting a thumbs-up from everyone before you move forward. It stops partitioning in its tracks, keeping our digital gold safe.
By deploying these strategies, we boost security big time.
Cryptographic Solutions for Secure Blockchain Transactions
Now, let’s keep our transactions safe. Cryptography is our best friend here. It’s the super-smart math that locks down our data. It turns our transactions into puzzles that only the right keys can solve.
One way we keep things tight is with something called hashing. It’s like making a digital fingerprint for data. If a single thing changes in the transaction, the fingerprint won’t match. No match, no entry — simple as that.
But sometimes, hackers try to impersonate others — classic Sybil attacks. So we use digital signatures. They make sure the person sending the blockchain data is who they say they are. Think of them as unforgeable digital autographs.
And let’s not forget about good old-fashioned vigilance. We constantly look for odd behavior on the network. Are there nodes acting strangely? Is someone trying to fake an identity? Staying alert means stopping problems before they start.
Put all these together, and we have a powerhouse defense. Cybersecurity is no joke, especially in blockchain. It’s about keeping everyone’s digital treasures locked up tight. With the right moves, we can shield our transactions and keep our blocks connected, just like Fort Knox keeps its gold secure.
Strengthening the Blockchain Ecosystem: Best Practices in Network Protection
Blockchain Node Security Best Practices
Keeping blockchain safe is like guarding a treasure. Bad guys try to mess with the network to steal or cause chaos. To stop them, we must be smart and use the best tricks to protect our nodes.
Lock your node down tight. Just like you wouldn’t leave your house open, don’t leave your node exposed. Use strong passwords and keep your software updated. This might seem simple but it’s super important.
Check who you’re talking to. On the blockchain, nodes talk to each other all the time. Use lists of trusted nodes to prevent bad actors from sneaking in. It’s like not opening the door to strangers.
Mix up how you connect. Attackers might try to block or watch where your data goes. Shake them off by using different paths. It’s like taking different routes to school to avoid bullies.
Assessing and Improving Blockchain Route Stability
Making sure data travels safely is key to protecting blockchain. It’s like ensuring the road to your home is safe from hazards.
Map out network paths. You have to know where data travels to spot problems. Use tools to see network paths. It’s like using a map to plan your road trip.
Spot traffic jams. If data slows down or stops, it could mean an attack. Watch for delays. It’s like keeping an eye on roadblocks so you can find another way.
Keep paths flexible. When one way gets risky, switch to another. Build networks that can change routes quickly. It’s like having a detour ready for a closed road.
By doing these things, we build a digital fort that’s tough to crack. We make sure bad guys can’t harm our blockchain gold.
We’ve explored serious threats to blockchain through routing attacks and their impact. We know that attackers can disrupt operations, but we’ve got ways to fight back. Securing decentralized ledgers is about being proactive—set up the right defenses and use tough protocols to keep the network resilient. We also looked at how cryptography acts as a shield, helping stop partitioning attacks and keeping transactions safe. Finally, it’s all about keeping our blockchain ecosystem strong. This means following best practices for node security and checking regularly to make sure our paths for data are stable. Stay sharp, stay secure, and the blockchain stays solid. It’s on us to keep our defenses up and adapt as threats evolve. Let’s do it right.
Q&A :
What are routing attacks on blockchain networks?
Routing attacks in blockchain networks happen when attackers exploit the data flow in a blockchain’s underlying network infrastructure, such as the internet. These attacks aim to intercept, alter, or disrupt the communication between nodes, potentially leading to delayed transaction confirmations, double-spending, or privacy leaks.
How do routing attacks affect blockchain security?
Routing attacks can significantly compromise the security and functionality of a blockchain. They can enable attackers to isolate and control parts of the network, allowing for malicious activities like the manipulation of transaction data, censorship of certain transactions, or even a 51% attack if significant hash power is isolated.
Can routing attacks be prevented on blockchain networks?
Although it’s challenging to entirely prevent routing attacks, there are measures to mitigate them. Blockchain networks can employ enhanced encryption protocols, peer-to-peer communication methods, or use dedicated and secure channels for important communications. Network monitoring for unusual activity can also be implemented to detect possible attacks early.
What is BGP hijacking, and how does it relate to routing attacks on blockchains?
BGP hijacking is a specific type of routing attack where the attacker takes control of the Border Gateway Protocol (BGP) tables by falsely announcing ownership of IP address blocks. As blockchains rely on internet connectivity to disseminate information across nodes, BGP hijacking can allow attackers to reroute blockchain traffic through malicious nodes, thus executing a routing attack.
Are all blockchain networks equally vulnerable to routing attacks?
Different blockchain networks may have varying levels of vulnerability to routing attacks depending on their design, consensus mechanisms, and network infrastructure. Networks that rely on more centralized points or have fewer nodes are generally more susceptible. Continuously enhancing security measures and network protocols is essential for reducing the risk of routing attacks.


RELATED POSTS
What are the challenges of blockchain: Navigating the Obstacles Ahead
What are the challenges of...
Security of Proof of Stake: Is Your Digital Investment Safe?
Enhance PoS Security! Learn about...
Grass Airdrop Stage 2 is almost here – Don’t miss out!
Successfully navigating the Grass Airdrop...
Blockchain Security Audits: Essential Shields Against Cyber Threats
Understanding the Importance of Blockchain...
How to Choose a Crypto Wallet: Secure Your Digital Fortune
How to choose a crypto...
Explanation of Proof of Work: How PoW Secures Blockchain Innovation
Explanation of Proof of Work...
Inter Blockchain Communication: Unveiling the Future of Cryptocurrency Connectivity
What is Inter Blockchain Communication...
Advantages of Blockchain Transparency: Unveiling the Trust Revolution
Unlock the Advantages of Blockchain...
Can you short on Coinbase Pro?
Can you short on Coinbase...
Future of On-Chain Code Audits: Revolutionizing Collaborative Cybersecurity
Enhance blockchain security with on-chain...
Blockchain Backlash: Uncovering the Environmental Footprint
The Environmental Impact of Blockchain:...
Moonwalk Fitness Airdrop – Guide to Participate and Receive Rewards
Moonwalk Fitness Airdrop offers a...
What is the ALIENX Airdrop and How to Participate Effectively
Do you want to invest...
What are the three advantages of using blockchain technology
Curious about “What are the...
What is a frontrunning attack? Is Your Transaction Safe?
Gain insight into the mechanics...
Unlocking Digital Wealth: Mastering Software Development Kits in Crypto
Unlock the Potential of Crypto...