I know the fear of losing hard-earned crypto keeps you up at night. But fear no more – I’m here to arm you with the knowledge you need to shield your digital treasure from DoS attacks on blockchain. These attacks aim right for blockchain’s core, choking networks and nodes until they cough up their strengths. We’re going to dive into the mechanics behind these assaults and pinpoint their favorite hangouts. Then, we beef up your defenses by laying out no-nonsense strategies to keep your blockchain fortress unbreakable. Stay with me, and let’s turn your blockchain into an impenetrable stronghold against cyber threats.
Understanding the Risk: How DoS Attacks Target Blockchain Networks
The Mechanics of Denial of Service in Distributed Systems
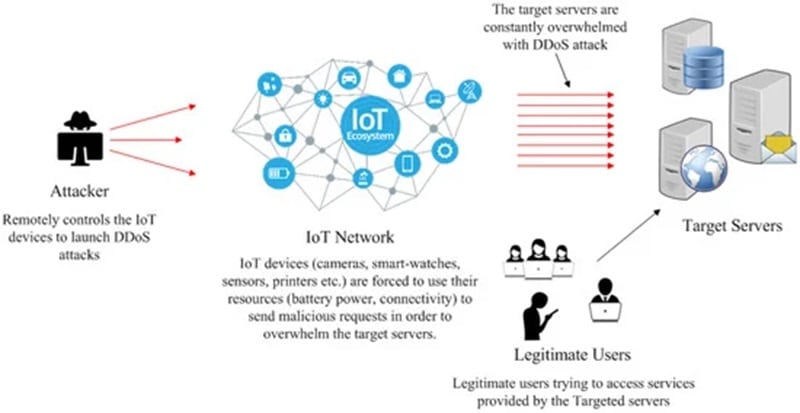
A denial of service attack aims to shut down a machine or network. Attackers overload systems with traffic. This stops normal service. Imagine a road so packed with cars that no one can move. That’s what happens to blockchain networks during these attacks.
In blockchain, this can mean many things. The attack might target a specific part of the network or try to flood the entire system. It may also disrupt essential communication between nodes. These are the different computers connected in the blockchain.
Distributed networks rely on many nodes. This is both a strength and weakness. Each node holds a copy of the blockchain ledger. Attackers probe these nodes for soft spots. If they find a weak node, they can block important info from spreading. This can slow down or even stop transactions.
Attackers also love to go after blockchain’s proof of work systems. These need a lot of computing power. An attacker sends fake requests to overwork the system. This can be bad, especially if the blockchain handles a lot of transactions.
Recognizing Vulnerabilities: From Node to Network
Nodes are key to blockchain’s strength but can be its weak spot. If a node has poor security, it’s an easy target. Attackers can take control of it. Sometimes they even manage to take over most of the network. This can lead to a scary situation called a 51% attack. Here, hackers change transaction records.
Smart contracts can also have weaknesses. These are the rules that make transactions happen automatically. If a smart contract has flaws, attackers use these to break into the network. They can change how transactions happen or stop them altogether.
Spamming is another way attackers mess with blockchains. They start loads of tiny transactions that don’t mean anything. But they clog the system like junk mail. This can lead to a big mess and slow the network down a lot.
To keep a blockchain safe, we need strong network security. We have to watch out for signs of an attack. Being ready is key. We can stop attackers before they cause real trouble. We can also spread the load. This means using many different computers to handle the work. So, if one computer gets attacked, the others keep the system running.
We have to check the blockchain ledger’s integrity too. Think of it like making sure a list of important steps is always right. This helps keep the record of transactions safe and accurate.
Blockchains should be able to grow without losing security. We can’t let them become less safe as they get bigger. We need to keep them tough against attacks. This means thinking ahead and always improving security.
For example, crypto platforms have to be ready to fight off a DDoS attack. These are the nasty attacks that try to take down websites by overloading them.
And here’s the thing, a well-protected blockchain can push back against these attacks. Anti-DDoS technology helps. It’s like having the best guards at your castle gates. They spot trouble fast and keep enemies away.
In short, blockchains are powerful but can be under threat. We must keep them as tight as ships. So, let’s build them strong, keep them safe, and make sure there’s a plan for when things go rough.
And remember, if we keep our blockchain networks tough and ready, we can trust them to take care of our crypto. We can beat the attackers at their own game.
Fortifying Your Defenses: Strategies for Blockchain DDoS Attack Prevention
Implementing Robust Network Security Protocols
To keep a blockchain safe from denial of service (DoS) attacks, you start with strong network security protocols. Think of these as rules that guard against hackers and system overloads. It’s like building a digital fortress where each rule is a thick wall against cyber attacks.
The first line of defense is to make sure each part of the network checks the others. Think of proof of work like a lock that keeps track of who does what. It’s one way networks make sure users are real and not fakes trying to break in. This helps stop a blockchain disruption by keeping the system fair and hard to cheat.
Another guard is watching how much each user can do at once. By setting limits on how much a user can send, it’s harder to flood the network. It’s like making sure no one can eat all the cookies and leave none for others. This keeps the network running smooth and fast.
Strengthening Node Resilience and Availability
Now, let’s dive into nodes. Nodes are like the workers of blockchain, each holding a copy of the digital ledger. But, if too many nodes go down, the blockchain can crash. That’s where node strength comes in. It’s making sure that each node can handle a ton of work without breaking a sweat.
Let’s talk about node availability. This means having enough nodes ready to step in if others are busy or under attack. It’s like having extra players on a sports team. Even if some are tired, there’s always someone fresh to play. This way, the blockchain keeps going, no matter what.
To make nodes really tough, we set them up to handle cyber threats on their own. If they spot a threat, they react right away. This is like teaching each worker to deal with problems as they come. It helps the whole system stay safe and run smoothly.
And, don’t forget – keeping real-time checks on the blockchain helps too. It’s like having a guard do rounds, seeing if anything looks odd. These checks can catch bad stuff before it gets worse. They’re a key part of stopping network floods and protecting the blockchain from losing service.
In a nutshell, a safe blockchain needs strong rules, tough nodes, and a smart lookout system. By mixing these tools, we build a secure place for your crypto. It’s all about staying ahead of trouble and keeping the digital cash moving without fear of attack. With these steps, we aim to boost blockchain health and keep your crypto secure against the bad guys.
Proactive Measures: Ensuring Continuous Protection Against Cyber Threats
Real-Time Monitoring: Detecting and Responding to Anomalies
To keep our crypto safe, we need to watch all blockchain activities closely. Imagine having a top-notch security system in your home. You could see everything happening, all the time, right? For blockchains, it’s much the same. We set up a system that looks for weird or unusual activity. This is what we call real-time monitoring.
Now, let’s talk about how this happens. We use smart tech that checks the blockchain’s pulse, like a health app on your phone. It scans the system and sends us alerts when something’s not right. This is good because we can spot trouble fast and act on it quicker.
What sort of stuff are we looking for? Things like an unexpected number of transactions or a user sending too much data. These could be hints that a denial of service attack might be coming. When we see this, we jump into action to keep our blockchain safe.
Designing Redundancy Plans and Load Balancing Solutions
Ever heard the saying, “Don’t put all your eggs in one basket?” Well, that’s what we do with blockchains. We spread out the work and resources. This way, if one part gets hit by a cyber threat, the rest keeps working fine. This is known as a redundancy plan.
For a blockchain, we build extra, backup systems. They are ready to take over if the main system gets attacked or goes down. Think of them like spare tires. You hope you won’t need them, but they’re lifesavers when you do.
Next up, we have load balancing. This is a bit like a traffic cop for data. It shares work evenly across different systems and paths. It helps because during an attack, having this balance means less change of a single part getting overwhelmed. Load balancing also helps our blockchain handle a lot of users without slowing down.
Remember, denial of service attacks on blockchains aim to flood the system with too much traffic. So, with plans like these, we stay ready for anything. We want smooth sailing, even when cyber storms come our way.
Taking care of our crypto is a big job. But with the right steps, like watching for risks and having backups, we can keep our digital treasure safe from harm. In the end, it’s all about not giving cyber threats a chance to make trouble. And that’s what keeps your crypto secure.
Beyond Prevention: Building a Resilient Blockchain Ecosystem
Securing Smart Contracts and Mitigating Transaction Spamming
Smart contracts seal deals without the need for a middle man. But, they can have flaws. Hackers may attack, aiming to steal crypto or jam the system. We must find and fix these smart contract weaknesses.
I always remind folks, the key is testing and keeping an eye on the code. This helps catch issues before they turn into big problems. For example, if a contract is public, anyone can spot bugs. The community can then work together to patch them up quick.
Another headache is transaction spamming. This can slow down a network fast. Imagine loads of junk mail but for crypto. It clogs the system so real deals can’t get through. To stop this, we put “rules” in place that limit the noise. These rules can block user actions that look shady or are excessive.
A smart move here is to use rate limiting on decentralized networks. This sets a cap on user actions within a timeframe. If someone tries to flood the system with too many transactions too fast, the system says “no more” until a set time passes.
Future-Proofing: Scaling Your Blockchain without Compromising on Security
A big question is, can you grow your blockchain and stay secure? Yes, you can! But it needs careful planning.
Scaling means more users and more deals. But if not done right, it opens doors for attackers. When scaling up, keep an eye out for denial of service blockchain threats. These try to overload the system and cause a blockchain service outage.
We can scale and guard against these threats with a bit of smart design. This includes using more than one path for deals to flow. It’s like having extra lanes on a highway. If one gets jammed, others keep moving. This is part of what we call blockchain infrastructure protection.
Also, check your consensus mechanisms security. This is the rule book that everyone in the network follows to agree on what’s valid. Some old styles, like proof of work, are strong but can use a lot of power and get bogged down as more users join. Others, like proof of stake or delegated proof of stake, can be quicker. But each has its pros and cons when it comes to security.
In the end, the aim is to strike a balance. You want your blockchain to handle more activity without getting thrown off by cyber threats to digital ledgers. It takes teamwork, smart tech, and always staying a step ahead. This way your crypto is safe, and the network can handle whatever comes its way.
In this post, we explored how denial-of-service attacks hit blockchain networks. We learned that weaknesses can exist, from a single node to the whole network. To protect ourselves, it’s crucial to use strong security steps and make sure each node is tough and always up. This means keeping an eye on the system all the time and having backup plans and ways to manage lots of traffic.
Having a solid blockchain is more than just stopping attacks. It’s about setting up smart contracts right and handling lots of transactions without letting security slip. As we move forward, we must grow our blockchain systems smartly, with safety in mind. Remember, a secure network means peace of mind for everyone using it. Let’s stay alert and keep building stronger blockchains!
Q&A :
What exactly are DoS attacks on blockchain?
DoS, or Denial of Service attacks, specifically target the reliability and availability of blockchain networks. In a DoS attack, adversaries attempt to overwhelm the network with a flood of transactions or other forms of data, aiming to disrupt normal operations and prevent legitimate users from accessing blockchain services.
How can DoS attacks impact the performance of blockchain systems?
When a blockchain system encounters a DoS attack, its performance can significantly deteriorate. Network latency may increase due to the excess traffic, leading to slower transaction processing times. In severe cases, the blockchain may become temporarily unavailable, causing delays and potential financial losses for users.
Are there any known vulnerabilities in blockchain that make it susceptible to DoS attacks?
Blockchain technology, like any other, has potential vulnerabilities that could be exploited by attackers. Some blockchains might be more vulnerable due to protocol design choices, such as smaller block sizes or a less robust network infrastructure. Additionally, smart contracts with flaws can sometimes be exploited to facilitate DoS attacks on the blockchain.
What measures can be taken to prevent DoS attacks on blockchain networks?
To prevent DoS attacks, blockchain networks can implement a range of security measures. These can include rigorous network monitoring, rate-limiting transaction requests, employing anti-spam algorithms, and utilizing consensus mechanisms designed with DoS resistance in mind. Increasing network scale and diversity can also fortify a blockchain against potential DoS attacks.
How do blockchain platforms recover from a successful DoS attack?
Recovery from a DoS attack on a blockchain platform involves several steps. Initially, it’s necessary to identify and neutralize the source of the attack. Following this, the network may undergo stress tests and security audits to reinforce vulnerable points. Updates and patches can be rolled out to mitigate the exploited vulnerabilities, and user communication is crucial to maintaining trust and ensuring transparency throughout the recovery process.

RELATED POSTS
Blockchain Security Essentials: Navigating the Regulatory Terrain
Understanding the Regulatory Landscape for...
Disruptive potential of blockchain technology: Shaping Future
Unlocking the disruptive potential of...
Decentralized Learning Unveiled: Blockchain’s Trailblazing Educational Platforms
Blockchain-Powered Learning Platforms: Examining Decentralized...
Yala Airdrop – A Great Opportunity to Earn Free Tokens Today
Discover Yala Airdrop now –...
GRVT Airdrop – The 2 Most Important Expectations
The GRVT Airdrop offers a...
Blockchain in Government: Revolutionizing Public Sector Transparency and Efficiency
Enhance trust in government with...
Key Challenges in Blockchain Research: Navigating the Uncharted Digital Terrain
Key challenges in blockchain research:...
Mechanics Of Blockchain Technology: How It’s Transforming Tech
Learn the Mechanics of Blockchain...
Explore Top DePin AI Projects
Exploring the leading DePin AI...
Bitcoin Golden Cross – Strategic Investment Solution
The Bitcoin Golden Cross is not...
Vulnerabilities Identified: Is Your Smart Contract Exposed?
Critical smart contract security issues...
Revolutionizing the Classroom: How Blockchain Will Transform Education
Enhance education with blockchain! Strengthen...
Understanding Audit Findings and Recommendations: Unveiling the Secrets to Financial Health
"Understanding audit findings and recommendations:...
Gradient Network Airdrop – How to Earn Points and Receive Rewards
Are you ready to dive...
Bitcoin Charlotte and 3 Expected Growth Signals
Bitcoin Charlotte is not just...
Peer-to-Peer Learning Unlocked: Harnessing Blockchain for Collaborative Education
Blockchain's role in peer-to-peer learning:...