In the blockchain world, trust is the spine of its existence. But guess what can snap it in a flash? A 51% attack. This is not a far-fetched scenario where the majority rules; it’s a real threat where someone with more than half of the mining power can take control. How does a 51% attack work? Simple: they get the power to reject valid transactions or spend the same digital coins twice. It’s like having the keys to the kingdom and the crown jewels are at risk. Let’s dive into understanding the mechanics of this attack, peel back the layers of blockchain’s security, and figure out how to protect your digital treasure chest from these digital sieges.
Understanding the Mechanics of a 51% Attack
The Role of Hash Power in Blockchain Security
Imagine blockchain like a digital ledger. Each page of this ledger needs a seal. This seal is made by miners who solve complex math problems. They do this to add a block of data to the chain safely. The one with the most computing power (hash power) gets to seal the page.
But what if someone gets over half the seal making power? They might harm the ledger pages. This is what folks call a 51 percent attack. This person controls the blockchain as they can now add and seal pages. This is a big no-no for security.
Consensus Mechanisms and Vulnerability to Attacks
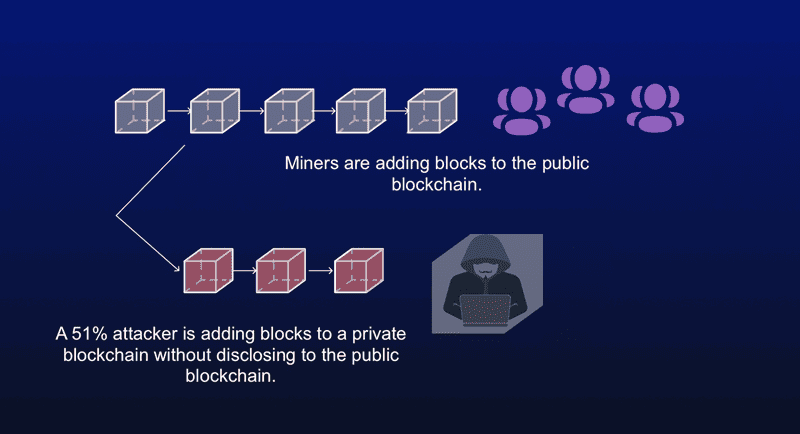
When I say “consensus mechanisms”, I mean rules all users follow to add blocks. They agree to trust the longest chain of blocks. But, if one has over half the power, they can make a longer chain in secret. Then, they can show it suddenly. Their chain becomes the trusted one. This is bad. It lets them control new pages and even change old ones.
To stop a 51 percent attack, we need lots of miners. The more we have, the harder it is for one to get too much power. Think like a team sport. If one player tries to play all positions, it’s easy to spot and stop them.
Knowing all of this helps us protect our blockchain from big dangers. So, we keep an eye on who’s got hash power. We make mining a team effort which stops any player from getting too strong.
Everyone with a coin is part of the team. When we work together, we keep our money safe.
The Consequences of Gaining Majority Control
Double Spending and Blockchain Integrity Threats
Think of a 51% attack like a game where one player gets too powerful. This can let them break rules. Suddenly, they can spend their coins twice. This is double spending. It is not fair play and it messes up trust in the game. In the real world, bad actors can do this to blockchain. They need more than half of the network’s mining power. They take control and can stop new transactions or undo old ones. This hurts trust and can make prices fall fast.
Many people work hard to keep the blockchain safe. They check all the work, called Proof of Work. But if someone messes with this, we all must be on guard. This is not just about money. It’s about security and faith in the system. If that goes away, the whole thing can fall apart.
Historical Major Cryptocurrency Attacks and Their Impact
Let’s talk history. It’s like story time but with big effects. In 2016, Ethereum was hit hard. A project on it called “The DAO” got attacked. Hackers took millions in ether. How? It was through a weakness not in the blockchain, but in the project’s code.
Then in 2018, something else happened. A lesser-known coin, Verge, got attacked. This showed us even small coins need good defense. Attackers can mess with transactions or make coins from thin air. Not good.
Here’s another one: Bitcoin Gold. It’s like Bitcoin’s cousin and it got hit twice in 2018. Big trouble for trust and the coin’s value. These stories ring alarms for Bitcoin too. Bitcoin is big and strong, but it shows that caution is key. Even big players aren’t safe all the time.
We need to learn from these. Investors and miners need to team up for safety. They need to put a lot of computers to work. And they need to mix up who gets to add to the blockchain. It’s like having different goalies in a game. It keeps things safe.
Attacks don’t just steal money; they steal peace of mind. After all, trust makes this world go ’round. So, when a 51% attack happens, it can shake us all. It’s super important to watch out for mining pool dominance. Big groups shouldn’t control too much power.
Take proof of stake systems. They use different rules than mining. They count how much coin you hold. This can help stop power grabs, but it’s still new. We need to do more tests and checks to be sure.
Just remember: blockchain is not just tech talk. It’s a promise to keep things safe and fair. When that promise breaks, we see prices drop and trust vanish. We must work together to keep the promises true. Protect the network, and we protect the future. It’s a team effort, guys. Let’s win this game fair and square.
Mitigation and Defense Strategies against 51% Attacks
Network Security Measures and Hash Rate Monitoring
Blockchains get strong by many people checking and agreeing on all transactions. This stops one person from having full power. But when someone controls more than half the computing power in a blockchain network, we have a big problem. We call this a 51 percent attack.
In this attack, the bad guys can double spend coins. This means they spend the same coin many times. Everyone in the network believes them because they have the most power. This is bad for the blockchain and for people’s trust in it.
To stop these attacks, networks watch their hash power. Hash power is like the muscle of the blockchain. The more you have, the stronger your say in the network. Watch for sudden changes in who has this power. Bad guys might be trying to get more than they should.
Networks also add security measures. They check transactions more carefully. They need more confirmations before they believe a transaction is good. This makes it harder to double spend.
The Importance of Decentralization in Mitigating Risks
Being spread out is key for blockchains. It’s like having many locks on a door. You need all the keys to open it. If one group gets all the keys (that’s hash power), they can do bad things, like steal money or mess up the transactions.
To keep things safe, blockchains need to stay spread out. This means no one miner or group should have too much power. If everyone helps to check the transactions, it’s harder for a bad group to take over.
So, remember, for blockchains to stay safe, we need:
- Everyone watching and keeping hash power balanced.
- Tough rules to check transactions.
- Many different people running the network.
By doing this, we help keep blockchains safe. We can trust our digital money. And we can keep building a future where everyone plays by the rules.
Proactive and Reactive Responses to Network Compromises
Ethical Hacking and Blockchain Security Testing
Imagine a fortress with guards watching 24/7. Now, think of a blockchain in the same way. It’s a digital fortress, and the guards are ethical hackers. They’re the good guys who test the walls and alarms. Their job is to find weak spots before the bad guys do.
Ethical hacking helps us know where a blockchain can fall; where it’s not so strong. They use their skills to check how well a blockchain can fight off attacks. One of the meanest attacks is the 51 percent attack. That’s when someone grabs more than half the power on a network.
So, when someone tries to control the chain, these hackers can tell. They look at how much power miners have. If one miner or a group starts to get too strong, it’s a red flag. They tell us so we can act fast.
Preparing for Recovery from a 51% Attack
Now, let’s talk about getting back up after a fall. If a 51 percent attack happens, things can go south real quick. Double spending may occur, and users could lose trust. That’s like breaking the rules of why we have blockchains.
We plan how to bounce back from such hits. We study past attacks on Bitcoin and others to learn lessons. We see how attackers could get in and stop them next time. It’s about having a strong plan to fix what goes wrong. We think about the worst to make sure people’s coins stay safe.
Recovery means seeing the attack early and shouting it out loud. Then, we decide how to stop it right away. We must also let users know what’s happening. Honesty is big here – no keeping secrets.
Next, fixing the blockchain comes. We clean up any mess from the attack. This way, the chain becomes strong once more. Some will check every part of the chain to make sure it’s all good. Others will figure out if any coins got stolen.
For recovery, we also think about how to help those who lost coins. We talk with exchanges and users. We need them all to play a part in getting things back to normal.
Recovery isn’t just about fixing; it’s learning. It’s making sure we can stand tall if another attack ever comes. Every fail teaches us how to be better at keeping the chain safe.
These are big jobs to do. They need folks who know the blockchain game. That’s why people like me put on our capes. We dive deep into the tech and find ways to keep your digital coins snug as a bug. We stand guard so you can rest easy knowing your crypto is safe.
In this post, we dug into what a 51% attack means for blockchain and why hash power matters. We looked at how these attacks can shake trust by allowing double spending, with real cases showing the damage done. We also covered how to fight back with stronger security and keeping networks spread out.
To sum it up, staying safe from a 51% attack calls for constant vigilance, smart defense plans, and always aiming for a wide net of control. It’s a mix of tech smarts and teamwork. Remember, good guys can use the same tools to test and strengthen our systems.
Keep your coins safe and your knowledge sharper; that’s the way to block these threats and keep the blockchain strong.
Q&A :
What is a 51% attack in the context of cryptocurrency?
A 51% attack occurs when a single miner or group of miners gains control of more than 50% of a blockchain network’s mining power, hashrate, or computational power. This majority control enables the attackers to modify the blockchain’s ledger, potentially double-spending coins, and preventing other miners from completing blocks. The attack undermines the blockchain’s decentralized and trustless nature, leading to security breaches and loss of confidence in the network.
How can someone execute a 51% attack?
To execute a 51% attack, the attacker must accumulate more than half of the network’s mining power. This can be achieved by acquiring a massive amount of mining hardware, colluding with powerful mining pools, or exploiting security vulnerabilities in the network. Once in control, the attacker can reject legitimate blocks mined by others and replace them with their own, allowing for the reversal of transactions, stopping new transactions from gaining confirmations, and ultimately harming the network’s integrity.
What cryptocurrencies are most vulnerable to a 51% attack?
Cryptocurrencies with a lower total network hashrate are generally more susceptible to a 51% attack. Typically, smaller or newer cryptocurrencies with less distributed and lower-powered mining networks face a greater risk, as it is cheaper and easier for attackers to gain the majority of mining power. Coins that use proof-of-work (PoW) algorithms, especially those with fewer active miners, are at a higher risk compared to those with large, diverse miner ecosystems.
What are the consequences of a 51% attack on a cryptocurrency?
The consequences of a 51% attack can be severe. They include double-spending of the cryptocurrency, where the attacker spends the same digital tokens more than once. It can also result in disrupted transactions, reduced network security, and potentially a significant loss of user confidence. The diminishment of trust can lead to a decrease in the coin’s value and harm the overall perception of cryptocurrency security.
How can blockchain networks prevent 51% attacks?
To prevent 51% attacks, blockchain networks can implement various measures such as increasing the number of miners to ensure a more distributed control of the hashrate, using more robust consensus algorithms like proof-of-stake (PoS) that are less vulnerable to such attacks, or employing a hybrid model combining PoW with other systems. Additionally, networks may adopt defensive strategies like network monitoring for anomalous hash power activity, adjusting confirmation times to require more confirmations for a transaction, and encouraging decentralized and varied mining operations.


RELATED POSTS
How Security Bolsters Blockchain Adoption: Navigating the Tech Maze
How does security impact blockchain...
Explanation of Proof of Work: How PoW Secures Blockchain Innovation
Explanation of Proof of Work...
Impact of Consensus Algorithms: Bolstering or Breaking Security?
Explore the impact of consensus...
Vulnerabilities Identified: Is Your Smart Contract Exposed?
Critical smart contract security issues...
Emerging Consensus Mechanisms for Blockchain: The Future of Decentralized Validation
Emerging consensus mechanisms for blockchain....
Cryptocurrency Ro Khanna and the future of regulation
Discover how cryptocurrency ro khanna...
Blockchain and Bureaucracy: How will governments use blockchain in the future?
How will governments use blockchain...
Unveiling Types of Crypto Derivatives: Your Ultimate Guide to Digital Asset Trading
Discover the Mechanics of Bitcoin...
Can blockchain track pharmaceuticals throughout the supply chain?
Can blockchain track pharmaceuticals throughout...
Aligned Layer Airdrop – Perfect Ownership Roadmap of ZK Quiz NFT
Aligned Layer Airdrop offers users...
CoinList and U2U Network – Partnering to Build the Future of Decentralized Infrastructure
The cryptocurrency market is witnessing...
What is a Web3 ecosystem? Web3 NFT Marketplace? The future of digital asset trading
The Web3 ecosystem is revolutionizing...
Decentralized Learning Unveiled: Blockchain’s Trailblazing Educational Platforms
Blockchain-Powered Learning Platforms: Examining Decentralized...
What is Karak? Guide to joining Restaking
In the dynamic cryptocurrency market...
Acki Nacki Airdrop: A detailed guide on how to participate
In the rapidly evolving world...
Unveiling Cryptocurrency’s New Frontier: What is NFT?
What is NFT cryptocurrency? Learn...