In the world of digital wealth, your assets face threats you can’t see—like Replay attacks on blockchain. I’ll show you how they strike and why you should care. Thieves could replay past transactions, draining your crypto without a trace. But don’t worry, I’ve got the tricks to help you stand guard. We’ll dive deep into the nuts and bolts of these attacks, and I’ll arm you with top-notch defenses. Read on to turn your blockchain fortress from vulnerable to invincible!
Understanding Replay Attacks in the Blockchain Ecosystem
Defining Replay Attacks and Their Impact on Digital Assets
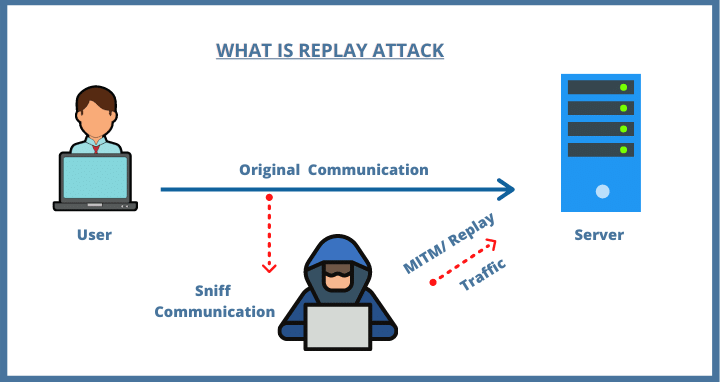
Imagine if someone took your money twice without asking. That’s like a replay attack. Replay attacks can happen when digital info is not safe. They are like copying a transaction to steal money or mess things up. Kids, think of it as if someone took your homework, erased your name, and put theirs. Not cool, right?
A crypto thief can do a replay attack to take coins twice. This hurts people by stealing their digital money. It makes everyone upset and not trust the system. We must stop these cheats to keep our digital money safe.
Common Techniques Employed in Replay Attacks
In the blockchain world, double-spending is a big no-no. It’s like spending the same dollar twice. Replay attacks can cause it. The bad guy uses the same data as a real transaction to trick the network. And boom, they spend the same coin two times!
There are ways to keep safe from replay attacks. Some blockchains use unique transaction IDs. This helps to tell apart the real deals from the fakes. Also, upgrading the whole system with things like SegWit helps. SegWit makes transactions safer and harder to mess with.
Different blockchains talk to each other. And just like friends trade Pokémon cards, chains can share weakness. This can make replay attacks spread through many systems. It’s like a sickness that moves from one to another.
Network security is like a club’s secret handshake. It’s a way to make sure everyone follows the rules. This can help stop bad things, like replay attacks, from hurting the blockchain.
Think of your digital wallet like a toy chest. You want a good lock to keep your things safe. Digital signatures act like secret codes to lock your wallet. They keep your coins from getting stolen.
Blockchains sometimes split into two, kind of like when a road forks. This can be done on purpose, like a hard fork, or more smooth, like a soft fork. Each kind has different risks for replay attacks. So, smart people make new rules to help keep everyone’s coins from being taken in a replay attack.
Being careful with changes to the systems helps to keep them safe. Peer-to-peer networks are like a big team working together to check each other. This teamwork keeps things running right and helps to push bad players out.
We must always be on the lookout to make sure all transactions are good ones. This way, we keep everyone’s digital money safe. When you know how replay attacks work, you can help stop them. Together, we can keep our blockchain toys from being taken by bullies.
Now you see how important it is to keep our digital playground safe. Replay attacks are scary, but now we know how to play it safe.
Strengthening Wallet and Network Defenses Against Replay Attacks
Implementing Robust Wallet Security Measures
Have you ever thought your money was safe, only to find out someone took it without asking? It’s like when you think you’ve locked up your bike, but a clever thief knows how to break the lock. Digital money, or cryptocurrency, needs strong locks too. Let’s talk about something called a replay attack. This is where someone takes a transaction you made and does it again without you knowing, to steal money.
Imagine you’re sending a digital coin to your friend. A replay attack could make it look like you sent the same coin twice. Not good, right? The key to stopping this is to make your wallet tough to break into. Think of a wallet as a digital safe where your cryptocurrencies like Bitcoin live. To make it strong, you need good locks, which are like secret codes that only you should know.
Passwords and secret keys are like the special numbers on your bike lock. If someone has them, they can get into your wallet. Each time you trade or send digital money, a digital signature proves it’s really you. This signature is your secret handshake with the network saying, “Yes, it’s me. Let this go through.” And just like a real signature, no two should be the same. If they are, someone might be in your wallet, and you don’t want that.
Leveraging Network Security Protocols to Safeguard Transactions
The blockchain is like a busy city where all the digital money moves around. Just like roads have rules and lights to keep cars from crashing, the blockchain has special ways to keep money safe as it moves. These rules are called network security protocols.
You might have heard of a thing called double-spending in cryptocurrency. It’s like if you try to buy two candy bars with the same dollar bill. Obviously, that’s not fair or possible in the real world, but in the digital world, we need rules to stop that from happening. By using network security protocols, we make sure each digital coin can only be spent once.
Sometimes the rules for how all the digital money works need to change. This can happen during something called a hard fork in the blockchain. When this happens, it’s like there’s a new set of house rules for everyone to follow. But not everyone may agree with the new rules, and that’s when things can go sideways. During these forks, the chain splits and replay attacks can sneak in.
So what do we do? We get everyone on the same page by using something called upgrade consensus. It’s like when your family agrees on where to go for dinner. If everyone agrees, there’s no fight, and things go smoothly.
Making sure everyone is working with the same rules stops replay attacks. This is because it’s harder for the bad guys to find a way in. When we do this, we keep our digital money safe and sound. Remember, in the world of digital coins, staying safe is like a game of keep-away. And you want to win that game every time.
Devising Strategies for Replay Attack Prevention and Mitigation
Hard Fork vs. Soft Fork: Protective Measures Against Replay Scenarios
When a blockchain splits, we call it a fork. A hard fork is a big change. It creates two paths—one that follows new rules and one that sticks to old ones. We’ve got a soft fork too. It’s a small tweak and doesn’t split the road. Both can stop replay attacks, where someone copies a transaction from one path to the other, causing trouble.
Imagine you pay for a toy using the old path. Someone can grab that payment, replay it on the new path, and buy another toy with your money! That’s not fair, right? A hard fork can help by making it clear which path a payment belongs to—you can’t use the same money on two paths. But if both paths look too much alike, confusion happens, and replays slip through.
Soft forks can also help prevent replays. They tighten up the rules bit by bit. This means fewer chances for the bad guys to copy your payment info. Plus, a soft fork doesn’t split the road entirely, making it less messy.
Outlining Cryptographic and Consensus Strategies to Thwart Replay Techniques
Now, let’s dig a bit deeper. To stop replay attacks, we use secret codes (that’s cryptographic tricks) and group decisions (that’s consensus strategies). We’re talking about heavy locks on our digital wallets and everyone agreeing on the security we use.
Secret codes, like digital signatures, lock your transactions. They’re like secret handshakes that only you and your friends know. Only the person with the right handshake can use your coins. This way, even if a bad guy grabs your payment, they can’t use it somewhere else.
Then there’s group decisions, like when everyone in the blockchain agrees to scribble unique numbers on every payment. This is like saying, “I saw this payment, and it’s for the old path only!” So if someone tries to replay it on the new path, everyone would know it doesn’t belong there.
Consensus tricks also include agreeing to follow new rules together. Sometimes, everyone decides it’s time to change things up for better safety. They might say, “Let’s all upgrade to this new and better path!” And like a team, they work together to keep everything secure.
So, we keep our coins safe from replay attacks through both secret codes and group power. Together, we’re building walls and keeping watch to protect our digital gold. Remember, even in the digital world, teamwork and smart locks make all the difference.
Ensuring Safe Execution of Transactions and Smart Contracts
Addressing Smart Contract Tamper Resistance
Smart contracts are like automatic deals. People trust them to work alone, no cheating. To keep this trust, we need strong smart contract tamper resistance. This means making sure no one changes the deal after it’s made.
First, we write code that’s tough to break. We set rules in the code that check for any tricks. If someone tries to mess with the code, the system knows and stops it. It’s like a lock that tells you someone’s been picking at it.
We also use tests and checks. Before the contract goes live, we try to break it on purpose. This shows us any weak spots we need to fix. Think of it like testing a bike helmet. You’d want to know it works before you need it.
Then, we keep an eye on it. Once live, we watch the contract and look for any funny business. Any weird activity could mean a tamper attempt. It’s checking the fence for holes regularly.
By doing all this, we make sure these smart contracts stay fair. No one can change the deal, and everyone knows what to expect.
Promoting Non-Replayable Transactions through Unique Identifiers and Upgraded Protocols
A replay attack is when someone reuses a transaction to steal. Like if a bank check got used more than once! To stop this, we need unique marks on each transaction. These are like barcodes, no two are the same.
We also upgrade our systems with new rules – protocols. Think of it like updating your game so it works better and no cheats work. We make rules that say only new, marked transactions can play. This leaves the old, used ones out.
Every time there’s a change in the system – like a hard fork – we’re on it. We add ways to tell new transactions from old. We want each one to have a special pass that only works once. This way, even if someone tries to reuse it, it won’t work.
Upgrades like SegWit help too. SegWit makes digital transactions safer, like adding seatbelts to cars. It adds more unique parts to each transaction, so repeating them gets even harder.
Another trick is changing the format. If two systems speak different ‘languages’, they can’t understand reused transactions. It’s like only accepting tickets with a new, special stamp – no stamp, no entry.
So, we work hard to keep your digital deals and money safe. We aim to stop the same trick from being played twice. Every transaction is a one-time ticket. This way, your digital things stay yours, and only yours.
By focusing on these areas, we keep your deals in smart contracts safe. And we make every transaction unique, stopping repeats. We’re always updating and checking, making a walled garden for your digital life. With these steps, we make sure no one gets a chance to play a transaction twice.
In this post, we’ve explored how replay attacks can threaten your digital assets. We’ve looked at what these attacks are and how they mess with transactions. You now know common tactics bad actors use to pull off these attacks. We’ve also shared strong tips on securing your wallet and using network defenses to keep your assets safe. We’ve examined both hard forks and soft forks, crucial for protecting your blockchain activities. Plus, we’ve discussed how smart contracts and unique transaction IDs can stop replays.
Our goal is for you to feel informed and prepared. Attacks can happen, but with the right steps, we can block them and keep our blockchain ecosystem safe. Stay alert, update your security, and you’ll be set to tackle these threats head-on. Keep these tips close, and your digital treasures will stay safe!
Q&A :
What is a replay attack in the context of blockchain?
A replay attack on blockchain is a security exploit where a valid data transmission is maliciously or fraudulently repeated or delayed. In blockchain networks, this typically occurs when a transaction from one blockchain is replicated on another chain without the permission of the sender, potentially leading to the unauthorized spending of tokens or assets.
How can you protect a blockchain from replay attacks?
To protect a blockchain from replay attacks, various measures can be taken, including using unique transaction IDs, implementing replay protection protocols that make transactions incompatible between different chains, and utilizing personal signatures to verify the legitimacy of each transaction. Some blockchain platforms also incorporate time stamps or network-specific information to prevent replays.
Are all blockchains susceptible to replay attacks?
Not all blockchains are equally susceptible to replay attacks. Blockchains that have strong replay protection mechanisms in place are less vulnerable. However, blockchains that are forks of other chains without proper measures for distinguishing transactions between them can be particularly at risk.
What happens to your assets during a replay attack?
During a replay attack, the attacker may replicate a transaction from one blockchain onto another, which can result in the unintended spending of the same assets on both chains. This could lead to financial losses for the asset holder if the secondary transaction is confirmed and the assets are transferred to the attacker or another unintended recipient.
Can replay attacks be reversed on the blockchain?
Replay attacks typically cannot be reversed once they have been executed, due to the immutable nature of blockchain transactions. However, if an attack is detected early, measures can sometimes be taken to prevent the replay transaction from being confirmed, thus protecting the assets. Ensuring strong security practices and using up-to-date wallets with replay protection are crucial to prevent such incidents.


RELATED POSTS
Blockchain Ballots: Revolutionizing Voter Fraud Prevention Systems
Examples of blockchain-based voter fraud...
What Makes the Connection Between Blockchain Technology and Cryptocurrencies Special?
Blockchain technology and cryptocurrencies form...
How to Avoid Crypto Wallet Scams: Foolproof Strategies for Digital Safety
How to avoid crypto wallet...
Security Challenges in DeFi: Navigating the Uncharted Waters Safely
Protect Your DeFi Applications from...
Blockchain Breakthrough: Blockchain In Supply Chain Management
Enhance supply chain management with...
Forgotten Runiverse: A promising NFT Game on Ronin Network
Forgotten Runiverse is emerging as...
Blockchain Breakthrough: How can blockchain improve patient data security
How can blockchain improve patient...
Future Trends in Blockchain Security: Staying Ahead of Threats
Future trends in blockchain security:...
Blockchain Security Companies Reviewed: Safeguarding the Digital Frontier
Leading Reviews of Blockchain Security...
Unveiling the Future: Impact of quantum computing on blockchain
The Impact of quantum computing...
Blockchain Revolution: Blockchain applications beyond cryptocurrency
Explore the vast applications of...
Security Challenges in Interoperable Blockchains: Navigating the Complex Web
Discover the security challenges in...
Routing Attacks on Blockchain Networks: Defending Your Digital Fort Knox
Understanding the Threat: How Routing...
Blockchain Revolution: Reducing Fraud In Student Records With Blockchain
Reducing fraud in student records...
Smart Alaya AI Blockchain Technology – The future of the world
Curious about the game-changing potential...
Unveiling Cryptocurrency’s New Frontier: What is NFT?
What is NFT cryptocurrency? Learn...