Curious about how Proof of Elapsed Time in Crypto is reshaping the blockchain landscape? This innovative consensus mechanism leverages randomness to create a more energy-efficient and secure mining process. Want to discover how it enhances scalability and trust in cryptocurrency transactions? Let’s explore the captivating world of PoET together!
Understanding the Core of the Proof of Elapsed Time in Crypto Consensus Mechanism
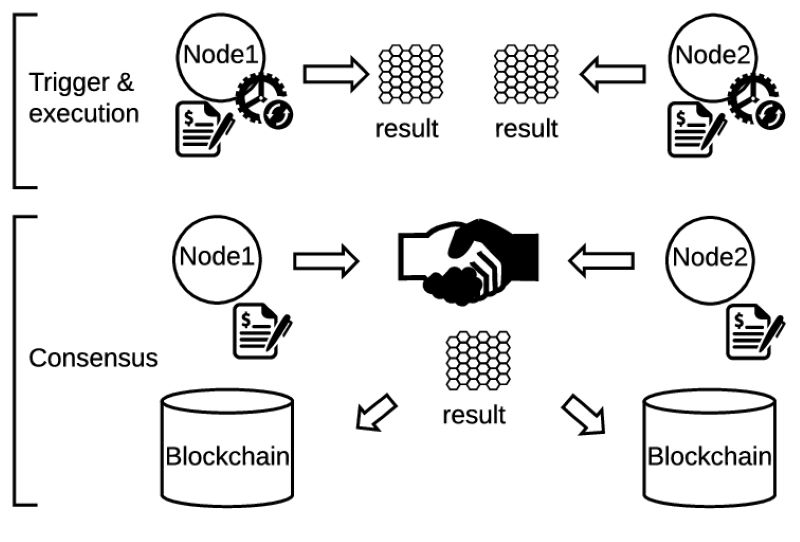
At the heart of secure blockchains lies a magic key: the cryptographic timer. Think of it as the stopwatch for the internet’s ledger book — the blockchain. In the Proof of Elapsed Time in Crypto consensus mechanism, this timer plays a clever role. It randomly selects who gets to add the next page to our book, ensuring fairness and security. This timer safeguards against any underhanded tactics, like someone trying to insert fraudulent entries.
Each node in our crypto ecosystem receives a random wait time from the timer. Imagine it as drawing straws but with a clock. When your timer goes off first, you win the opportunity to add a block. This method drastically reduces the energy consumption typically associated with traditional consensus models like Proof of Work. The process is like patiently waiting your turn at a deli counter — no rush, no energy wasted, just wait for the “bing!” and it’s your turn.
This timer not only ensures efficiency but also fortifies blockchain security. Without it, there would be a vulnerability to attacks. With Proof of Elapsed Time in Crypto, potential intruders must outsmart the timer, which is no easy task!
Implementing Intel Sawtooth Platform for PoET
Now, let’s discuss how we implement this timer in the real-world crypto landscape. That’s where the Intel Sawtooth platform comes into play. Intel provides a robust framework for developers to create their own blockchains, packed with features to enhance security and performance.
By leveraging Intel Sawtooth, developers choose an efficient and environmentally friendly approach to blockchain design. This platform empowers the Proof of Elapsed Time in Crypto to operate without consuming excessive energy. This efficiency is crucial for creating sustainable blockchain solutions while maintaining robust functionality.
Using this innovative platform ensures that every transaction adheres to the rules, making the blockchain a fair playing field. It’s akin to having a diligent hall monitor who never sleeps. This dependable platform facilitates scalability without the risks of slowdown or system failures. It allows Proof of Elapsed Time in Crypto to function smoothly, promoting fairness and trust within the ecosystem.
The Advantages of Proof of Elapsed Time in Crypto Over Traditional Consensus Models
Have you heard about crypto mining and its hefty energy requirements? Well, the Proof of Elapsed Time in Crypto presents a revolutionary alternative that’s significantly better for our planet. Unlike traditional methods, such as Proof of Work, which rely on energy-intensive computations, PoET employs a lottery-like system to select miners based on random wait times.
In the conventional Proof of Work model, computers race to solve complex mathematical puzzles. The first to succeed gets to add a new block to the blockchain, which requires enormous amounts of electricity. In contrast, Proof of Elapsed Time in Crypto gives each miner a random wait time determined by the cryptographic timer, reducing the energy footprint substantially. This method creates a fair environment, allowing miners with various resources to participate without draining energy.
How PoET Upholds Blockchain Network Security and Fairness
Safety and fairness are paramount in blockchain, and Proof of Elapsed Time in Crypto excels in both. With each block addition, miners receive a random wait time, ensuring that no one can manipulate the system. This randomness creates an equitable environment where everyone has an equal opportunity to succeed.
PoET employs trusted execution environments (TEEs) available on platforms like Intel Sawtooth. These TEEs act like a secure club where PoET rules are enforced, preventing any attempts at manipulation. With Proof of Elapsed Time in Crypto, we aren’t just hoping everything’s fine — each step is verified, maintaining the integrity of transactions and ensuring smooth operations.
Implementing PoET in Decentralized Systems
When securing valuable assets, the best defense is essential. The Proof of Elapsed Time in Crypto serves as a strong lock for our blockchain. Think of it like a secret code that protects your digital assets. Intel Sawtooth aids in implementing this mechanism, ensuring only authorized parties can add to the blockchain.
By using Proof of Elapsed Time in Crypto alongside TEEs, we create a robust environment where manipulations are nearly impossible. This setup guarantees that all transactions are conducted transparently and fairly.
Achieving Scalability and Efficiency in Permissioned Ledger Systems
For blockchains to thrive, they must be fast and capable of handling numerous transactions simultaneously — this is known as scalability. Proof of Elapsed Time in Crypto facilitates this within permissioned ledger systems, where membership is controlled. Participants are verified, and roles are clearly defined.
By integrating PoET, we enhance scalability without demanding excessive energy. While traditional consensus models consume vast amounts of energy, Proof of Elapsed Time in Crypto operates with efficiency. Each miner’s computer sits idle until their time comes, conserving energy.
The Future of Sustainable Blockchain with PoET
The perception of blockchain as a significant energy consumer is shifting, thanks to Proof of Elapsed Time in Crypto. This consensus mechanism demonstrates how to validate blocks without consuming vast quantities of power. Instead of tackling complex problems, PoET chooses miners through a fair wait time lottery.
This innovative approach ensures that all miners have an equal chance to contribute to the blockchain, promoting inclusivity and fairness. The cryptographic timer plays a vital role, selecting the winner based on their patience.
Exploring the Role of Smart Contract Execution in PoET Networks
In the blockchain realm, ledgers are dynamic entities, thanks to smart contracts. With Proof of Elapsed Time in Crypto, these contracts operate efficiently and securely on platforms like Intel Sawtooth. They execute transactions quickly, maintaining clarity and minimizing confusion.
Intel Sawtooth not only provides the necessary framework but also oversees smart contract operations, ensuring compliance with established protocols. This combination of PoET and Sawtooth guarantees that transactions are executed fairly and securely.
Proof of Elapsed Time in Crypto is not just a new consensus mechanism; it’s a significant advancement in safeguarding digital assets and minimizing environmental impact. By effectively combining energy efficiency with fairness, PoET is reshaping the future of blockchain and paving the way for a more sustainable cryptocurrency ecosystem.
If you want to stay updated and delve deeper into innovations in blockchain technology, don’t forget to follow us at Blockchain Global Network. Let’s explore and build the future of cryptocurrency together!
Q&A
- What is Proof of Elapsed Time in cryptocurrency?
Proof of Elapsed Time (PoET) is a consensus mechanism used in blockchain technology that aims to ensure fairness in the block creation process without requiring significant computational power. It relies on a trusted execution environment to randomly choose a leader based on the passage of time, allowing for energy-efficient block validation within the network.
- How does Proof of Elapsed Time ensure security in the blockchain?
PoET ensures blockchain security by using secure hardware that enforces random wait times for each participant. The system elects the participant with the shortest wait time to create the new block, making the process resistant to manipulation. This mechanism prevents the concentration of power and promotes decentralization, contributing to the security of the blockchain.
- Does Proof of Elapsed Time offer advantages over Proof of Work?
Yes, Proof of Elapsed Time offers several advantages over the Proof of Work (PoW) consensus mechanism. Notably, PoET is more energy-efficient as it doesn’t require large amounts of computational resources to validate transactions. Additionally, it provides a more level playing field for participants regardless of their computing power, reducing the risk of centralization present in PoW systems.
- Is Proof of Elapsed Time compatible with all types of cryptocurrencies?
Proof of Elapsed Time is not universally compatible with all types of cryptocurrencies. It’s a specific protocol designed for permissioned blockchain networks, such as Hyperledger Sawtooth. Cryptocurrencies must have a system architecture that supports a trusted execution environment to implement PoET successfully.
- Can Proof of Elapsed Time prevent 51% attacks in cryptocurrency?
Proof of Elapsed Time is designed to prevent the feasible execution of a 51% attack by reducing the influence of computational power in the validation process. Since leader selection is based on elapsed time within a trust-based environment, it is significantly more challenging for a single entity to control the majority of the network’s consensus power, thereby making a 51% attack less likely.


RELATED POSTS
How to Participate in the Avail Airdrop and Earn $AVAIL Tokens Breakthrough
Avail Airdrop offers a simple...
Blockchain Revolution: Securing Student Records for the Future
Discover the impact of blockchain...
Immutable Data Records: Unlocking the Secrets to Secure, Trustworthy Information Management
Discover the benefits of immutable...
Milena Mayorga: Influential person in El Salvador politics
Milena Mayorga, a prominent figure...
Comedian Airdrop – Token BAN Leads the Memecoin Trend
In the world of memecoins,...
Nillion Airdrop – Leading the Trend from Testnet to Mainnet
By participating in the Nillion...
Mitigating Risks of Majority Mining Attacks: Your Crypto Safety Plan
Mitigate risks of majority mining...
Decentralized Learning Unveiled: Blockchain’s Trailblazing Educational Platforms
Blockchain-Powered Learning Platforms: Examining Decentralized...
Security Challenges in DeFi: Navigating the Uncharted Waters Safely
Protect Your DeFi Applications from...
What is a honeypot in Crypto? Unveiling the Deceptive Traps!
What Is a Honeypot in...
Cost of Blockchain Security Audits: Are You Investing Wisely?
Understanding the Costs of Blockchain...
How is blockchain used in DeFi: Unlocking Financial Freedom
How is blockchain used in...
Timeline of Blockchain Development: A Revolutionary Tech Journey
Timeline of blockchain development: From...
What is a Doji Candle? Learn to identify market uncertainty
What is a Doji candle...
Blockchain Adoption Unveiled: Are Industries Embracing the Change?
Is blockchain widely used? Explore...
Public Key vs Private Key Cryptography: Unlocking the Secrets of Digital Security
Understanding the Basics of Public...