Public Key vs Private Key Cryptography: Let’s be honest, digital security is a beast we all grapple with. Terms like “encryption” and “cryptography” can seem like arcane magic. Yet, understanding the difference between public and private keys is crucial for anyone who uses the internet. Think of them as two sides of the same coin, each playing a vital role in keeping your digital life secure. Ready to dive in? I’ll walk you through the nuts and bolts of public key vs private key cryptography, and show you why these concepts are the linchpin of digital security—even if you’re not a tech wizard.
Understanding the Basics of Public and Private Key Cryptography
Asymmetric Encryption Basics
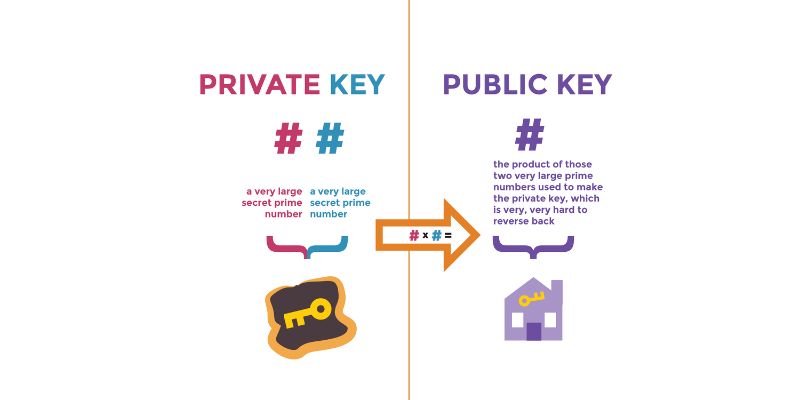
What are asymmetric encryption basics? Asymmetric encryption uses two keys, public and private. Each key does a unique job. The public key locks or encrypts data. Anyone can get this key. But, only the private key can unlock or decrypt what the public key protected. Think of the public key like a padlock you can close without a key. But, you need the right key to open it again.
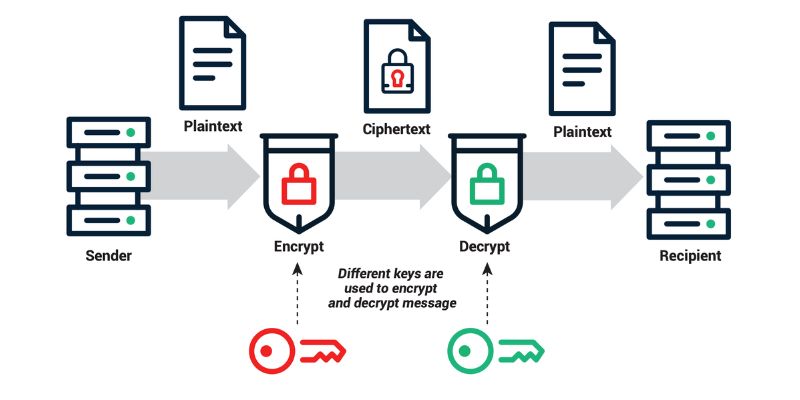
Asymmetric encryption keeps messages safe. It means only the right person can read them. It’s like sending a locked box through the mail. If you have the private key, you can open the box. Asymmetric encryption is also behind the digital signatures that check if a message is genuine and unaltered.
Cryptography Fundamentals
What are cryptography fundamentals? Cryptography is the art of secret writing. It uses math to hide or lock up information. This keeps our chats, bank details, and private stuff safe online. We have two main types: symmetric and asymmetric.
Symmetric encryption uses one key for locking and unlocking. It’s fast but needs safe key sharing. Asymmetric uses two different keys. It’s slower but better for safe sharing over the internet. Both types use algorithms, which are sets of rules for encrypting messages. They turn regular text into a code that’s hard to crack.
Cryptography keeps hackers away from our personal information. It uses keys and algorithms to lock up data. A key is like a real key, and an algorithm is like a safe’s combo. Long keys and smart algorithms make better protection. They make sure only the right person can unlock the message.
Digital signatures prove who sent the message. They use keys just like encrypting does. This signature shows the message is real and did not change in transit.
In summary, public and private keys form a team. They lock and unlock data, keeping secrets safe. They make sure personal stuff doesn’t fall into the wrong hands online. This is the foundation of internet safety for everyone.
Exploring the Differences: Symmetric vs Asymmetric Keys
Symmetric vs Asymmetric Encryption
Think about sending secret notes in class. Now imagine doing that on the internet. That’s where encryption comes in. It scrambles data so only the right people can read it. There are two main types: symmetric and asymmetric. They work differently to lock and unlock your secrets.
Symmetric keys use one key for both locking and unlocking data. It’s like having one key to lock your diary and the same one to open it. This method is fast, but there’s a catch. You have to share the key with anyone you want to read your diary. If the wrong person gets the key, they can read everything.
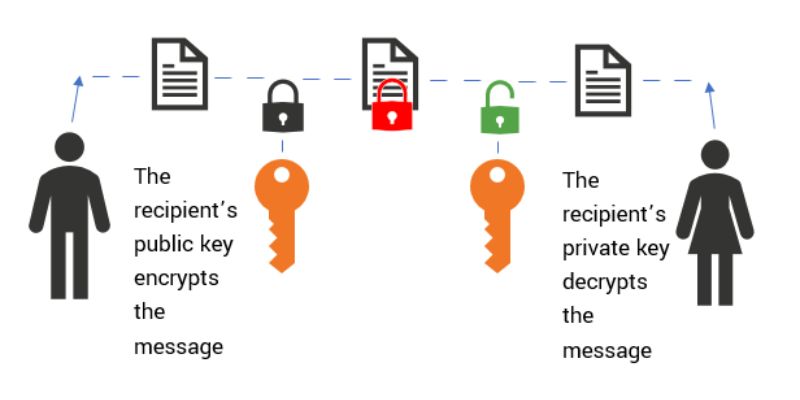
Asymmetric keys, on the other hand, use two related keys: a public key and a private key. The public key is out there for anyone to use. It’s like a mailbox on your fence where anyone can drop a message in. But, only you have the private key to open the mailbox and read the messages. This way, even if someone knows your public key, they can’t read your messages without the private key.
Key Pair Encryption Explained
Key pair encryption is like a secret handshake between two friends. When you send data, you lock it with your friend’s public key. Since it’s public, anyone can use it to lock messages. But only your friend has the matching private key to unlock it. It’s a smart way to keep messages safe.
The cool part about this system is digital signatures. Think of it as using your secret handshake to prove it’s really you. You use your private key to “sign” a message. Anyone with your public key can check that signature. If it matches up, they know the message is truly from you. It’s like signing a letter with a special pen that only you have.
With RSA encryption, these secret handshakes and signatures get super strong. It’s based on hard math problems that even smart computers can’t easily solve. So, your secret stays safe.
Remember, all these keys and lockboxes help us keep our online secrets. We use encryption for privacy, so no one can sneak a peek at our messages. Plus, it helps protect us from folks who might try to fake messages or steal sensitive info.
Sure, these ideas can get a bit tricky. But they’re the backbone of safe internet stuff, from websites to messages. As we share more online, understanding encryption helps us stay safe. It’s all about the right keys for the right locks, making sure our digital life is as private as our thoughts.
The Role of Encryption in Securing Data and Communications
Secure Communication Protocols
Let’s talk like we’re trading secret codes in a spy game, only this is real, and it’s about keeping our chats safe. When you send a message, you want it to land in the right hands—not any sneaky person trying to peek. That’s where secure communication protocols come in. Think of them like special rules everyone follows to keep things locked tight.
One big name in this game is SSL, or secure socket layer encryption. It’s like a magic spell that scrambles your message so only the right person can read it. But magic needs a key to work, right? Well, SSL uses something called transport layer security. It’s another set of rules that makes sure the magic is even stronger.
When you’re on the internet, seeing “https” in your web address means SSL is working. It’s telling you, “Hey, we’re using that magic spell to keep your visit to this website locked up safe.” It’s like a secret handshake between your computer and the website you’re visiting.
Cryptographic Algorithms and Encryption for Data Security
Now, let’s dive into the wizardry behind keeping data safe. The spells we’re talking about are called cryptographic algorithms. These are fancy steps that turn your message into a secret code. The cool thing is, there are lots of different spells, each with its own strength.
For example, there’s a tough spell called RSA encryption. It’s one of the heavy hitters in keeping your secrets safe. It works by using two keys, which are like secret decoder rings. One ring is public; you can show it to anyone. The other is private, and you’ve got to keep it under wraps. This tag team can lock up a message so tight, only the right person can open it up again with their private decoder ring.
Then there’s secret key cryptography. It’s like a secret handshake where both sides know a special knock. Only those who know the knock can open the door and get the message. It’s great for when you and your friend both know the secret, but not great when you’ve got a lot of friends because then you need a lot of special knocks!
Encryption is really all about keeping your stuff out of the wrong hands. Whether you’re saving important files or sending off a top-secret text, these spells make sure only the people you trust can see what you’re sharing. It’s like having the best lock on your diary, and only giving the key to your best friend.
We’ve just dipped our toes into the ocean of “encryption for data security”. But even from here, we can see how encryption is like a loyal guard, always on duty to protect our digital treasures. Remember, whether it’s a simple spell or a powerful RSA enchantment, the goal is always the same: keeping our secrets, well, secret.
Advanced Topics in Cryptography
Public Key Infrastructure and PKI Process
Public Key Infrastructure (PKI) is like a secret code club. The club uses special keys to keep messages safe. To join, you need two keys: one public, one private. The public key is like your club ID. You share it with everyone. The private key is your secret handshake. You never tell anyone.
The PKI process makes sure no one sneaks into the club. It checks IDs (public keys) to make sure they’re real. It also uses a trusted friend, called a Certificate Authority (CA), to vouch for new members. The CA’s job is to give out IDs and teach the secret handshake (private keys).
Imagine sending a secret note in class. You lock it with your friend’s locker combo (their public key). Only their secret key can open it. Even if someone else gets the note, they can’t read it without the combo. This is like encryption for privacy.
When you get a note back, you check to make sure it’s really from them. The note has a special mark (digital signature), showing it’s not fake. This signature uses the PKI process so you can trust the note.
Cryptosystems in Cybersecurity and the Future of Encryption
Cryptosystems are like forts, protecting our digital world. They guard our secrets, from texts to bank info. In cybersecurity, they block hackers and keep data safe. The future of encryption looks bright, with bigger and stronger forts being built every day.
Right now, we use keys – a bunch of random numbers – to lock or unlock our forts (encrypt and decrypt messages). RSA encryption is one type. It uses really big key numbers. The bigger the key, the harder it is to break in.
Secret key cryptography uses one key to lock and unlock. It’s faster than using two keys but you need to keep the key safe. If someone finds it, they can unlock everything.
Asymmetric cryptography is cooler. It uses two keys, one for locking and one for unlocking. It’s like having a special pen that writes notes only one person can read.
The Diffie-Hellman key exchange is like a secret handshake that lets two people make up a key together. They can do this without anyone else finding out, even if they’re listening.
Encrypting messages must stay a step ahead of hackers. So experts keep creating new methods. They study patterns and try to make better locks. They look at things like elliptic curves to make keys even harder to guess.
In the future, encryption will use quantum computers. They work super fast and can solve harder puzzles. This will make our forts almost impossible to break into.
But no fort is perfect. Things like private key misuse and weak keys can be a problem. Experts keep an eye out for these to keep the forts safe.
We will keep finding ways to make encryption stronger. This way, everyone’s digital secrets, from love notes to important bank info, stay safe. Strong cryptosystems are heroes in the fight for online safety.
In this post, we’ve dived into the world of cryptography, breaking down the basics alongside the more advanced topics. We started by explaining public and private keys—essential for secure online chats and data protection. Then we compared symmetric and asymmetric keys, showing the unique role each plays in encryption.
We also discussed how these tools help keep our digital talks and files safe. With secure protocols and algorithms, your private info stays out of the wrong hands. Finally, we looked ahead at public key infrastructure and its growing part in cybersecurity.
To wrap it up, I want you to feel confident about encryption. It protects our daily digital life, from sending messages to safeguarding sensitive information. Keep in mind, the future of online security relies heavily on the progress of cryptography. Stay aware, stay secure!
Q&A :
What is the difference between a public key and a private key in cryptography?
Public and private keys are part of asymmetric cryptography, which is a method that uses a pair of keys for secure communications. A public key is shared and can be distributed widely to encrypt data. A private key is kept secret and is used to decrypt the data that was encrypted with the public key. The two keys are mathematically linked, yet it is virtually impossible to derive the private key from the public key.
How does public key cryptography enhance security?
Public key cryptography enhances security by using two separate keys for encryption and decryption processes, which means that a user can freely distribute their public key without compromising the security of their private key. This allows for the establishment of secure communication channels over unsecured networks, like the internet, because only the intended recipient, who holds the corresponding private key, can decrypt the message.
Can you explain how public key and private key are used in digital signatures?
Digital signatures use public key cryptography to verify the authenticity of digital documents or messages. The sender applies a digital signature using their private key, which can be verified by others using the sender’s public key. This ensures that the document or message has not been altered in transit and confirms the identity of the sender, as only the owner of the private key could have created the signature.
What makes a private key secure in public key cryptography?
The security of a private key comes from its confidentiality; it must remain exclusively accessible to the owner. As long as the private key is kept secret, even if the public key is known, unauthorized parties cannot decrypt messages or forge authentic digital signatures. The algorithms used to generate the key pair are designed such that deriving the private key from the public key is computationally infeasible.
Is public key or private key more important for security?
Both keys are equally important for the security of the system. The public key is essential for anyone to be able to encrypt information for the key’s owner or verify a signature made by the owner’s private key. However, the private key’s security is more crucial because it must remain confidential to preserve the integrity of the encryption and the authenticity of the digital signatures. If the private key is compromised, the security of the communication is undermined.

RELATED POSTS
Cost of Blockchain Security Audits: Are You Investing Wisely?
Understanding the Costs of Blockchain...
Blockchain Efficiency Unlocked: Cutting Costs Seamlessly with Tech
How does blockchain reduce costs?...
Security Implications of Blockchain Sharding: Breaking Down Risks and Rewards
Understanding the Security Implications of...
Green Crypto Coins: Investing in a Sustainable Digital Future
Understanding the Future of Sustainable...
What is the purpose of blockchain technology?
What is the purpose of...
Bitcoin surges to $72,000 ahead of the U.S. elections
Bitcoin has experienced an impressive...
Government Regulations on Blockchain: Navigating the Crypto Maze
Understanding the Impact of Government...
Blockchain and Bureaucracy: How will governments use blockchain in the future?
How will governments use blockchain...
James Seyffart: A leading expert on ETFs and Cryptocurrency
James Seyffart is a prominent...
Fishwar Airdrop – Play to Earn on the Sei Blockchain
Fishwar Airdrop, a prominent project...
Unveiling Coinhive: What’s The Buzz About This Crypto Miner?
What is Coinhive? Learn about...
Exploring the Bitcoin Halving Cycle – Future and Price Predictions
Exploring the Bitcoin Halving Cycle...
The dApp Meaning – The Digital Revolution
Curious about “The dApp Meaning“?...
Exploring Liquid Staking in Crypto: Unlocking 24/7 Earnings Potential
"Explore liquid staking in the...
Blockchain Breakthroughs: Specific examples of future blockchain use cases
Revolutionize Financial Operations with Blockchain:...
What is a 51% attack? How a Blockchain Takeover Threatens Your Crypto
What is a 51% attack?...