The ICMP Protocol (Internet Control Message Protocol) plays a crucial role in network systems, supporting traffic management, error detection, and device availability. In this article, we’ll delve into the structure, functions, and common ICMP message types. This knowledge will help you improve the performance and stability of the networks you manage.
Understanding the ICMP protocol
What is the ICMP protocol?
ICMP (Internet Control Message Protocol) is a network protocol within the Network Layer of the OSI model and is a vital component of the IP (Internet Protocol). Developed in the 1980s, ICMP enables network devices to communicate and respond to each other via diagnostic and control messages. Its main purpose is to provide network status information and error messages when issues arise during data transmission.
Why is the ICMP protocol important?
ICMP Protocol is essential in maintaining connections and monitoring devices within network systems. This protocol is used to send error messages, check connection statuses, and determine whether destination devices can receive packets. One notable application of the ICMP Protocol is the “ping” command, a tool network administrators frequently use to check the availability of destination devices.
When a network device sends a packet to a destination but receives no response, ICMP Protocol can return error messages such as “Destination Unreachable” or “Time Exceeded,” indicating that the packet could not reach its destination due to time constraints or other issues. These messages allow network administrators to quickly identify the location and cause of a problem, enabling them to take timely corrective actions and ensure uninterrupted network traffic.
Practical applications of the ICMP protocol in network management
ICMP Protocol is not only a support tool for network administrators in monitoring network performance, but it also plays an important role in network security. This protocol can help detect network attacks, particularly in cases of denial-of-service (DoS) attacks. Some IDS (Intrusion Detection Systems) and IPS (Intrusion Prevention Systems) integrate ICMP Protocol to detect suspicious or invalid traffic.
Another practical application of ICMP Protocol is in network analysis tools like “Traceroute.” This tool uses ICMP messages to identify and map the path of a packet from source to destination, displaying each node (router) the packet passes through. With this, network administrators can pinpoint areas of congestion or faults in the transmission process.
ICMP and other protocols
While ICMP Protocol is a part of IP, it is not a data transport protocol like TCP or UDP. ICMP Protocol does not carry user data but is used solely to send control and error reporting messages, optimizing network processing and response times. Defined in RFC 792 and using IPv4, ICMP was later expanded into ICMPv6 for IPv6 networks, with additional improvements to support modern network systems.
Thus, ICMP Protocol is an indispensable component of modern network systems, supporting traffic management, error detection, and network connection optimization. A solid understanding of ICMP provides network administrators with many benefits, enabling them to maintain and enhance the stability, performance, and security of the network.
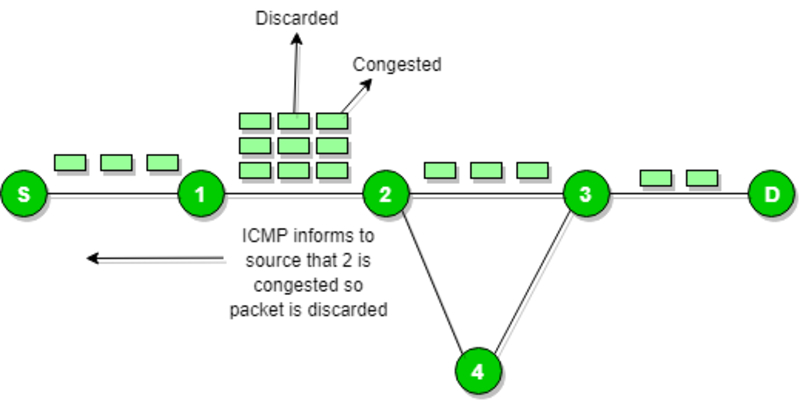
The structure of ICMP protocol
ICMP Protocol is designed with a simple yet highly efficient structure, consisting of two main parts: the header and the data. Each part has a specific role in defining and handling ICMP messages as they are transmitted across the network.
ICMP header
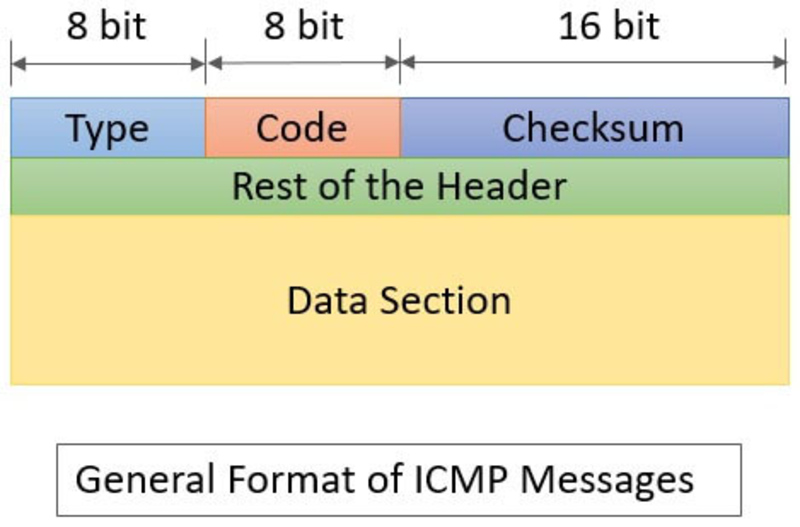
The ICMP packet header contains necessary data fields to define and verify the integrity of the ICMP message. Key fields include:
- Type: This field defines the type of ICMP message, indicating whether it is a request, a reply, or a specific error message. The Type value could be 0 (Echo Reply), 3 (Destination Unreachable), 5 (Redirect), or other types depending on the purpose of the packet.
- Code: Paired with the Type field, it provides details about the message’s content. Each Type can have multiple Codes to describe the message reason more specifically. For instance, with Type = 3 (Destination Unreachable), the Code could be 0 (network unreachable) or 1 (host unreachable), specifying why the packet could not reach its destination.
- Checksum: This field ensures data integrity in the ICMP packet. When an ICMP packet is created, the checksum is calculated and placed in the header. Upon reaching its destination, the checksum is recalculated to confirm the data remains error-free during transmission.
ICMP data section
The data section in an ICMP packet contains additional information, often error details or network status information. For messages like Echo Request and Echo Reply, the data may contain data sent from the sender to the receiver, allowing the receiver to reply to verify connectivity.
In the case of ICMP error messages, the data section can contain the header of the problematic IP packet along with trailing data, enabling network devices to identify the original packet and determine where the error occurred.
The role of ICMP header fields in message processing
The ICMP header acts as a guide for network devices on how to process each type of message. The Type and Code fields provide basic information about the message type, helping devices identify the purpose of the ICMP packet and determine the appropriate processing method. Meanwhile, the Checksum field ensures data integrity during transmission, enhancing this protocol’s reliability.
Key parameters in the ICMP protocol
ICMP Protocol includes three primary parameters: Type, Code, and Checksum. These parameters help define the message type, the reason for the message, and ensure data integrity.
Type
The Type field in an ICMP packet is an 8-bit integer that defines the ICMP message type. It’s a critical part of the header, indicating the packet’s purpose and guiding the system on handling the packet. Common ICMP message Types include:
- Echo reply (Type 0): Used to respond to echo requests from another device on the network. When a device sends a “ping” command to another device, the recipient will send back an ICMP Type 0 packet to confirm that the connection is active.
- Destination unreachable (Type 3): This message is sent when a device cannot reach the destination for some reason. Possible causes include an unreachable destination address, blocked route, or lack of access permissions.
- Source quench (Type 4): This message is sent to the sender when the data transfer rate is too fast, requesting a reduction in speed to avoid overload.
- Redirect (Type 5): When a router detects a better path for a packet to reach its destination, it sends this message to the source device to update its route.
- Echo request (Type 8): This message type is used for connectivity tests. When sending a “ping,” the sender sends an ICMP Echo Request packet to the destination and waits for an echo reply.
The Type field not only helps define the purpose of the ICMP packet but also aids in network analysis and troubleshooting. By examining the Type field, network devices and administrators can quickly identify the type of message being transmitted and handle it accordingly.

Code
The Code field is an extension of the Type and is also an 8-bit integer. Each Type may have multiple Codes that further describe the message. For instance, for Type 3 (Destination Unreachable), there are the following codes:
- Code 0: Network unreachable – The network is inaccessible.
- Code 1: Host unreachable – The target device is unreachable.
- Code 2: Protocol unreachable – The protocol is unsupported on the target device.
- Code 3: Port unreachable – The port on the target device is unreachable.
- Code 4: Fragmentation needed – Fragmentation is required, but the fragmentation flag is not set.
With the Code field, ICMP can provide additional context for the messages, helping the receiving device and administrators understand the reason for the notification. This allows administrators to quickly identify and accurately troubleshoot network issues.
Checksum
Checksum is a 16-bit field that plays an essential role in ensuring that ICMP packet data remains intact during transmission. Checksum is calculated based on the entire content of the ICMP packet, including both the header and data.
When an ICMP packet is sent, the sending device calculates the checksum and attaches it to this field. Upon receiving the packet, the receiving device recalculates the checksum from the received data and compares it with the checksum in the packet. If the two checksum values don’t match, this indicates data corruption during transmission, and the packet will be discarded.
Checksum helps detect random errors that occur during data transmission. Through this, ICMP ensures message integrity and improves the reliability of message transmission between network devices.
Primary functions of the ICMP protocol
The ICMP Protocol is not a typical data transmission protocol; it is a tool for network management and control. Below are the main functions of ICMP Protocol within a network system:
Data flow control
ICMP Protocol helps control the flow of data by sending messages that request a reduction in transmission speed if overload is detected. For example, when a device sends data too quickly and an intermediary router cannot process it in time, ICMP Protocol will send a Source Quench (Type 4) message to the source device to request a slower transmission speed.
This mechanism not only helps regulate traffic effectively but also reduces network congestion. This is especially important in large enterprise networks, where traffic can spike at certain times, putting pressure on routers and leading to connection loss. By using ICMP Protocol messages to control flow, devices can maintain stable connections without compromising service quality.
Network error reporting
ICMP Protocol is an effective error reporting tool in networks, allowing devices to send error notifications to the source when issues arise during data transmission. Error messages like Destination Unreachable and Time Exceeded enable administrators to detect and locate issues quickly.
For example, if a packet cannot reach its destination due to access restrictions, the router sends a Destination Unreachable (Type 3) message to the source device to indicate that the destination is unreachable. If the packet transmission time exceeds the limit, a Time Exceeded (Type 11) message is sent to the source. These notifications enable administrators to pinpoint and resolve issues promptly.
Device availability check
ICMP Protocol is also used to check the availability of devices on the network, often achieved through the “ping” command. When a network administrator needs to verify if a target device is operational, they can send an ICMP Echo Request (Type 8). If the target device is active, it will send back an ICMP Echo Reply (Type 0), confirming that the connection is available.
This method is very useful in detecting device issues, allowing for quick identification of errors and disruptions on the network. If no reply is received, the administrator can determine that the target device is unavailable and proceed with further troubleshooting.

Common ICMP protocol message types
ICMP Protocol supports various message types with different purposes, optimizing network monitoring and management. Here are common ICMP Protocol message types and their specific functions:
- ICMP echo messages: ICMP Echo Request and Echo Reply are two common ICMP message types used to test the connection between two network devices. When a device sends an ICMP Echo Request, it is asking the target device to reply to confirm whether the connection is active. If an Echo Reply is received, it confirms that the target device is available. If not, the administrator may infer that there is a network connectivity issue.
- ICMP destination unreachable messages: When a router or network device cannot deliver a packet to its destination, it sends a Destination Unreachable message. This message type has multiple codes to specify the reason, for example: Network Unreachable: Unable to connect to the destination network.
Host Unreachable: Unable to reach the destination device. - ICMP parameter problem message: When there is an error in the IP packet parameters, a Parameter Problem message is sent to the source. This indicates an issue during IP packet processing and calls for adjustments or corrections.
- ICMP redirect message: The Redirect message is used when a router finds that the source device can find a more optimal path to deliver the packet. The router will send a Redirect message to instruct the source device to use a different route.
ICMP Protocol plays a crucial role in monitoring, managing, and maintaining network performance. Through message types like Echo, Destination Unreachable, and Redirect, ICMP enables administrators to detect, diagnose, and resolve network issues quickly and effectively. With its abilities in flow control, error reporting, and device availability checks, ICMP is an indispensable tool in network systems, helping to optimize connections and ensure system stability.
With this article, Blockchain Global Network has shared key information on the structure and function of ICMP Protocol in computer networks. Understanding ICMP Protocol can help you manage and handle network-related issues safely and effectively.

RELATED POSTS
Crypto Crashing and 3 important investment implications
Crypto Crashing has shaken the...
Seer Airdrop: A chance to receive free SEER Tokens
Seer Airdrop is attracting the...
MiCA: A new regulation or a restraint on Crypto?
Starting from December 30, the...
Future of Blockchain Technology in 2030 – Prospects and Potential Applications
The future of blockchain technology...
Bitcoin Charlotte and 3 Expected Growth Signals
Bitcoin Charlotte is not just...
Memefi Coin Airdrop: Airdrop Timeline and Launch of Memefi Token
The Memefi Coin Airdrop presents...
BlackRock and Citadel New Stock Exchange – What Awaits in the Future?
The BlackRock and Citadel New...
Wormhole Airdrop – Take Advantage of 3 Valuable Investment Opportunities
Wormhole Airdrop is not only...
Blum Airdrop – A Ready Guide to Earning Tokens
Blum Airdrop is a fantastic...
Your essential guide to crypto conference events 2025
As the blockchain space matures,...
Guide to voting in Project Catalyst
Ready to help build Cardano?...
What is Proof of Stake? A Deep Dive into Blockchain Consensus
In the rapidly evolving world...
GMCoin Airdrop: A great opportunity to earn free GMC Tokens
The GMCoin Airdrop offers a...
HOT!!! Notcoin Accuses Bidget of Lying!
Notcoin Accuses Bidget of Lying!!!...
Elastic Chain: The future of Layer-2 Blockchain networks
Elastic Chain ushers in a...
Not Pixel Airdrop – Optimize Profits from Pixel
To optimize profits from Not...