Author Archives: Editor
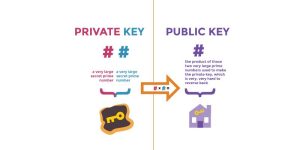
Public Key vs Private Key Cryptography: Unlocking the Secrets of Digital Security
Understanding the Basics of Public and Private Key Cryptography. Exploring the differences between symmetric and...
Cryptocurrencies and Digital Payments: Revolutionizing Modern Transactions
Understanding cryptocurrency transactions and blockchain technology. The mechanics of secure and transparent crypto payments. Embracing...
What is a frontrunning attack? Is Your Transaction Safe?
Gain insight into the mechanics of frontrunning crypto attacks. Understand transaction ordering dependence and blockchain...
What Is A Sybil Attack? Sybil Attacks Uncovered
What is a Sybil attack? Learn the nature of Sybil attacks, the role of Sybil...
Replay Attacks on Blockchain: Protecting Your Digital Assets
Protect your digital assets from replay attacks on the blockchain. Strengthen wallet defenses and implement...
How to Secure Private Keys: Your Essential Guide to Cryptographic Safety
Learn how to secure private keys with robust security measures, encryption, multifactor authentication, and secure...
DoS Attacks on Blockchain: Protecting Your Crypto from Cyber Threats
Protect Your Blockchain Network: Learn How DoS Attacks Target and Disrupt Distributed Systems. Strengthen Defense...
Security of Proof of Work: Is Your Cryptocurrency Safe?
Security of Proof of Work (PoW): Understanding vulnerabilities, attack prevention, and network security in blockchain...
Man-in-the-middle Attack On Blockchain: Can Really Be Compromised?
Protect Your Blockchain: Defend Against Man-in-the-Middle Attacks. Learn Vulnerabilities, Prevention Strategies & Transaction Security #BlockchainSecurity
Blockchain Unveiled: How Does Blockchain Technology Work
How does blockchain technology work? Delve into the mechanics of blockchain transactions, consensus mechanisms, and...