Different Types of Crypto Wallets offer varying levels of security and convenience for managing your digital assets. From the ease of hot wallets to the robust protection of cold storage, this guide explores it all. Learn how to set up a Ledger Nano X and boost your crypto security to new heights!
Different Types of Crypto Wallets
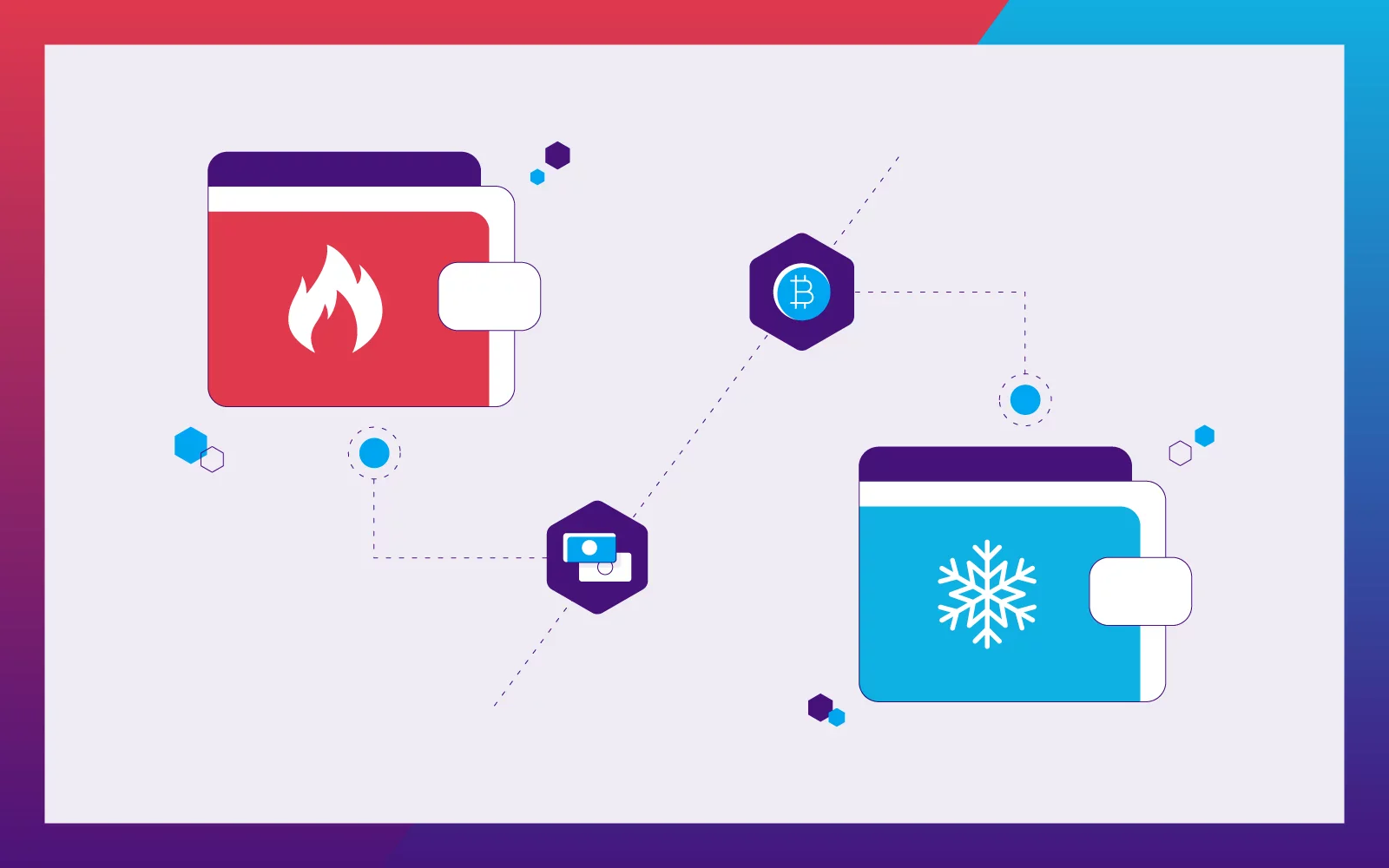
Hot Wallets – Quick and Easy Access, but with Risks
Hot wallets are like the digital equivalent of keeping your cash in your back pocket. These wallets are connected to the internet, making it easy for you to access and trade your crypto quickly. However, they come with a major downside—security risks.
- What are Hot Wallets?
Hot wallets include web-based wallets (like MetaMask), mobile apps (such as Trust Wallet), and desktop wallets (e.g., Exodus). They are perfect for users who need fast access to their crypto for trading or spending. - Security Risks
Since hot wallets are always online, they are more vulnerable to hacking and phishing attacks. Your private keys—what you use to access your funds—are stored within the wallet’s software, making them a target for cybercriminals. - Protecting Your Hot Wallet
If you choose to use a hot wallet, make sure to enable two-factor authentication (2FA) and use strong, unique passwords. Always be cautious about the websites you visit and the apps you download.
Cold Storage Options – Ultimate Security
When it comes to long-term security, cold storage is your best option. These wallets are offline, making them nearly invulnerable to online attacks.
- What is Cold Storage?
Cold wallets are offline wallets like hardware wallets and paper wallets. They offer the highest level of security because your private keys are not exposed to the internet. Examples of cold wallets include the Ledger Nano X, Trezor, and even paper wallets. - Benefits of Cold Storage
By keeping your cryptocurrency offline, you ensure that it is safe from hackers. The Ledger Nano X, for example, is a hardware wallet that connects to your computer or mobile device only when you need it. It stores your private keys securely within the device, and even if someone steals it, they cannot access your funds without the PIN and recovery phrase. - Setting Up Cold Storage
Setting up cold storage can seem intimidating, but it’s relatively simple. Devices like the Ledger Nano X guide you through the process, from creating a recovery phrase to securing your wallet with a PIN. Always remember to back up your recovery phrase in a safe place.
Hardware Wallets: Ultimate Security with Devices Like the Ledger Nano X
If you’re serious about security, hardware wallets are the way to go. These devices offer top-notch protection against theft and hacking.
- What are Hardware Wallets?
Hardware wallets like the Ledger Nano X are physical devices that store your private keys offline. To use them, you connect them to your computer or smartphone, input your PIN, and sign transactions.
- Why Choose the Ledger Nano X?
The Ledger Nano X is one of the most popular hardware wallets, offering Bluetooth connectivity for easy use with mobile devices. It supports a wide range of cryptocurrencies, allowing you to store multiple assets in one secure device. The Ledger Nano X is designed with both convenience and security in mind, offering a seamless user experience without compromising on safety.
- How to Set Up the Ledger Nano X
- Unbox your Ledger Nano X and connect it to your computer or mobile device.
- Write down your recovery phrase (this is essential for restoring your wallet if it’s lost or stolen).
- Set a PIN code for an added layer of security.
- Install the Ledger Live app to manage your assets, and you’re all set.
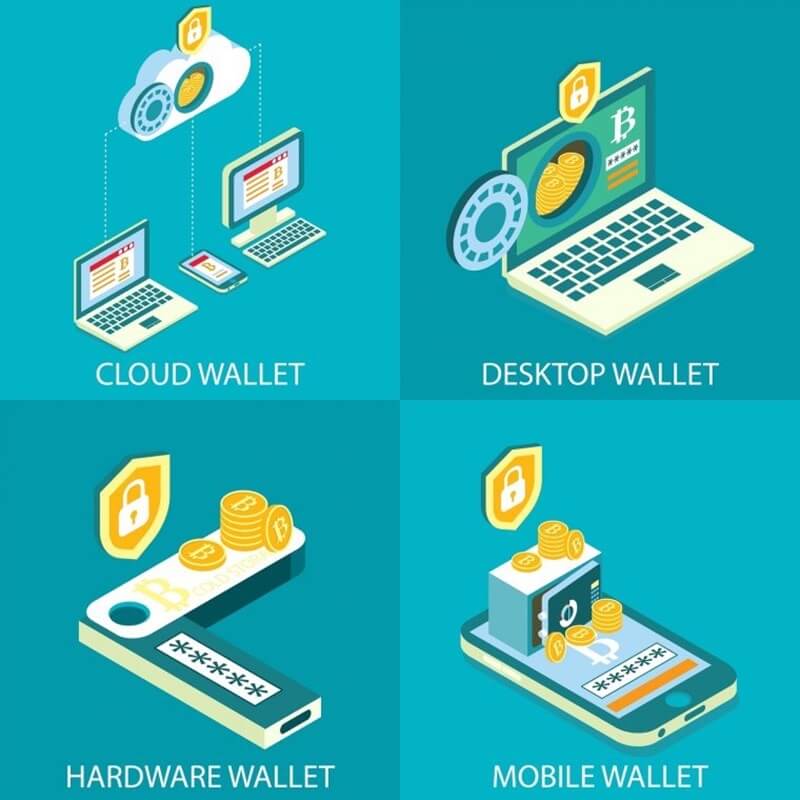
Software Wallets: Accessible Yet Vulnerable
For users who prioritize convenience, software wallets can offer a middle ground between hot wallets and hardware wallets.
- Desktop Wallets
Desktop wallets, like Exodus, are software applications installed on your computer. They store your private keys on your local device, providing more security than web wallets. However, they are still vulnerable to malware and viruses if your computer is compromised. - Mobile Wallets
Mobile wallets like Trust Wallet and MyEtherWallet allow you to manage your cryptocurrency on the go. While they offer the flexibility to trade and store crypto easily, it’s crucial to keep your phone secure. Use strong passwords and keep your phone updated to avoid vulnerabilities.
The Fort Knox of Crypto
Multisignature Wallets
Multisignature wallets require multiple private keys to authorize a transaction, offering extra security. Even if one key is compromised, your crypto remains safe. This is ideal for shared wallets or large holdings, reducing the risk of unauthorized access.
Wallet Encryption
Encryption scrambles your wallet’s data, ensuring only you can access it with the correct password. Strong encryption combined with a unique password keeps your crypto safe from hackers. Don’t forget: without the password, your wallet is nearly impossible to access.
Seed Phrases
A seed phrase is a series of words that restore your wallet if lost. Store it securely offline—don’t keep it digitally, as hackers can steal it. Multiple backups in different locations ensure that your funds are always recoverable.
Stay informed, stay secure! For more tips and updates, follow Blockchain Global Network to keep your digital assets protected and your crypto journey smooth!

RELATED POSTS
Can you mine Dogecoin? – Exploring the Mechanics behind it
Can you mine Dogecoin? This...
How Base L2 Sequencers are enabling the next generation of blockchain innovation
The evolution of blockchain technology...
Public Key vs Private Key Cryptography: Unlocking the Secrets of Digital Security
Understanding the Basics of Public...
BulbaSwap Airdrop: A unique investment opportunity in DeFi
BulbaSwap, a decentralized exchange (DEX)...
Vessel Finance: The DEX with near-zero gas fees
In the ever-evolving world of...
When was Blockchain Technology invented? A journey through its origins
Ever wondered, “When was blockchain...
Blockchain Crypto Technology – Transforming Traditional Finance with Decentralization
Curious about how Blockchain Crypto...
What is a Web3 ecosystem? Web3 NFT Marketplace? The future of digital asset trading
The Web3 ecosystem is revolutionizing...
What is blockchain technology in simple terms for beginner
What is blockchain technology in...
How does DALLE work? A Comprehensive guide to AI Art generation
How does DALLE work? This...
Smart Contracts: Unlocking Efficiency and Security in Transactions
Advantages of smart contracts -...
Near coin Revolution: Is this the Crypto you’ve been waiting for?
Near Coin is making waves...
Aligned Layer Airdrop – Perfect Ownership Roadmap of ZK Quiz NFT
Aligned Layer Airdrop offers users...
Trump Bitcoin reserve: A game changer for U.S. economy
The Trump Bitcoin reserve proposal...
Grindery Airdrop – Earn G1 and GX Tokens Easily!
Grindery airdrop, supported by Binance...
Essential Blockchain Technology Example Cases You Should Know
Blockchain technology example is everywhere,...