New threats to blockchain security are like digital termites, silently chipping away at your investments. As a burgeoning expert, I can’t stress enough the real, growing dangers targeting the backbone of your crypto assets. These threats are not just wild card attacks; they come bearing the sophisticated tech of quantum computing, itching to exploit even the slightest chink in the blockchain’s armor. They muscle in on crypto networks, twisting their evolving nature to their advantage. Your digital wallet won’t stand a chance if you’re not prepped for combat. It’s high time to get familiar with these risks. Buckle up as I guide you through the vulnerabilities that could leave your investments hanging by a thread and how to lock them down tight.
Understanding the Landscape of Blockchain Vulnerabilities
The Rise of Quantum Computing Risks
Quantum computers could break the crypto we trust today. So, how do they threaten blockchains? By unleashing massive computing power, strong enough to crack codes that keep our coins safe. Think of blockchain as a tough lock. Now, quantum computers are like master keys that could one day open these locks fast.
That’s scary, right? Not only could these super machines unravel encryption, but also they could let someone fake ownership of digital assets. This could mix up records and ownership on the blockchain in no time. We need new crypto methods that can face off with quantum threats. That’s the only way to keep our blockchain safe from quantum computers.
Crypto Network Attacks and Their Evolving Nature
Crypto network attacks come in many forms. As fast as we plug one hole, another pops up. One big worry is the 51% attack. What’s that? When a group gains more than half the network power, they can tamper with transaction records. They might reverse transactions or spend coins twice. It’s like letting a thief rewrite the ledger books.
Other dangers include Sybil attacks, where many fake identities swamp the network. This tricks the system into handing over control. And don’t forget about phishing scams. They trick you into sharing keys to your crypto wallet.
Our world runs on the web. So endpoint security in blockchain is crucial too. This means protecting the points where we connect to blockchain networks, like our smartphones or laptops. If they’re not safe, it’s like leaving our digital doors wide open for thieves.
Every type of attack, from dusting attacks that spot wallet activity, to ransomware that locks us out unless we pay up, puts our investments at risk. The stakes are high. But so is our drive to fight back. We work on better blockchain security measures like improving crypto network resilience. This is about making sure our systems bounce back even after attacks hit us.
So, what can we do? Patch up those software bugs in blockchain code sharpish. Zoom in on blockchain API security risks, those digital gateways that could let hackers in. Also, let’s get smart on how to shield our crypto exchanges from bad actors looking to break in.
We must stay one step ahead, always. Ramping up our blockchain hacking defenses. Preparing for that next big threat that no one saw coming. If we do this right, we keep our investments and our future in blockchain safe and sound. It’s on us to be the guardians of the digital treasure chest that is blockchain. Let’s ace it.
The Achilles Heel of Smart Contracts and Consensus Protocols
Scrutinizing Smart Contract Weaknesses
Smart contracts are like the bosses of crypto deals. They make things happen without asking people. But they can have issues, like software bugs. These bugs let hackers break in and steal money. We see this with big money losses in the news.
Example:
Imagine a vault with a glitchy lock. If the code is wrong, a thief could sneak in. That’s what can happen with smart contracts. They should work right, but sometimes, one wrong line of code invites trouble.
We always need to check smart contracts very carefully. This means reading and testing the code a lot. If we find a mistake, we must fix it fast. This can stop thieves from taking advantage.
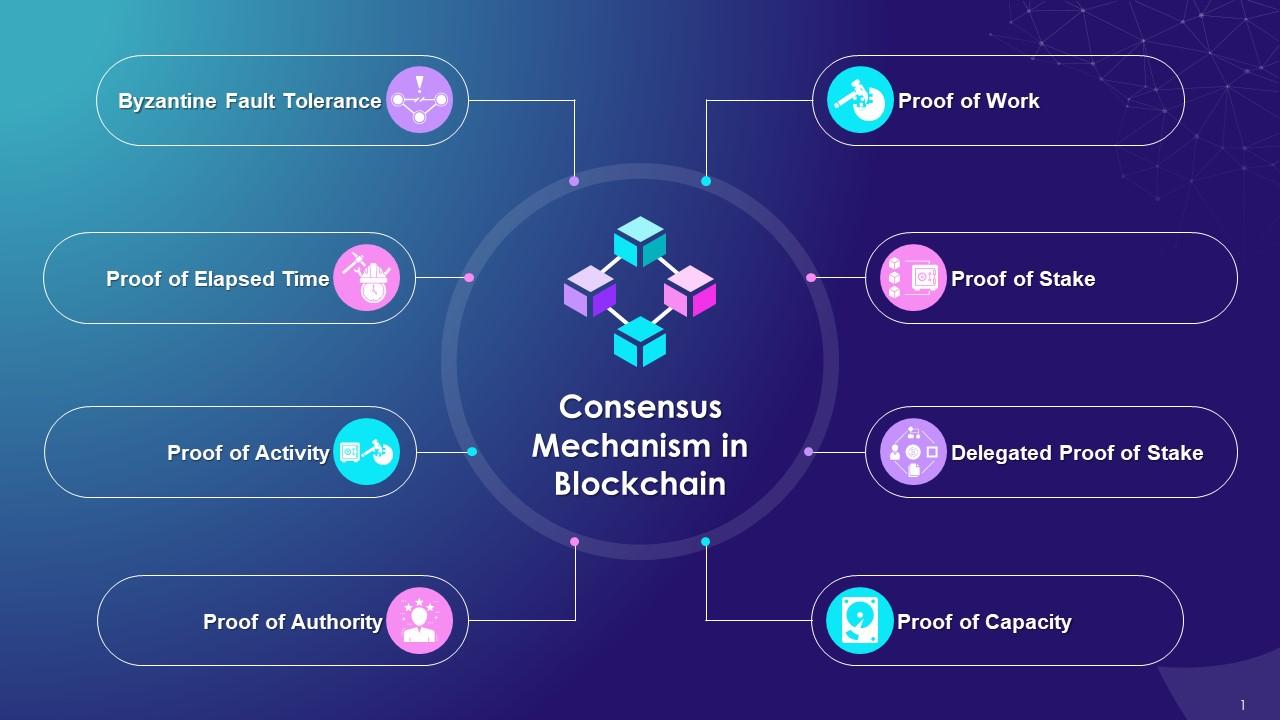
Consensus Protocol Flaws: Opening Doors to 51% and Sybil Attacks
Consensus protocols keep everyone agreeing in a blockchain. But they aren’t perfect. Things like 51% and Sybil attacks can hit them hard.
What is a 51% attack?
When someone controls over half of the mining power, they can mess with transactions. This can let them spend the same coin twice. This is like copying money in the real world – it’s cheating and hurts everyone.
Sybil attacks are also scary. In these, one user makes a lot of fake identities. They use these to gain extra power in the network. It’s like one person wearing many masks to trick others.
We must close these security gaps to keep our crypto safe. This means updating the way we agree in the network. We use new, smarter rules to stop these attacks.
In the blockchain world, being aware is key. Know that smart contracts can be weak spots. Understand that consensus protocols can fail. By checking contracts and improving how we agree, we stay one step ahead of the bad guys. Keeping crypto safe is about being smart and fast to act. Together, we can guard against these threats.
Safeguarding Your Digital Assets: Threats and Prevention
Endpoint Security in Blockchain: A Primer on Protection
Let’s chat about keeping your crypto safe, alright? Endpoint security – it’s like a guard for your device. It keeps nasty stuff from attacking your blockchain acts. Hackers, they sneak in through the smallest weak spots. We get endpoint security to block ’em.
Now, how does this thing work? Imagine locks on your doors and windows. Endpoint security does that, but for your computer. It puts up shields to stop hackers from stealing your crypto or messing with your blockchain. Simple but super important.
With endpoint security, you got to stay sharp. Hackers keep cooking up new tricks. They might try to trick you into downloading a virus. Or, they might attack the whole blockchain network. When they do, they could double-spend or shut down the system. No good, right?
So what can you do? First up, always keep your software updated. It’s like making sure your locks ain’t rusty. Then, be smart with your emails and links. One bad click and boom, hackers could sneak in. And of course, use strong antiviruses and firewalls. They’re like your 24/7 security guards.
Private Key and Crypto Wallet Security: Defending Against Emerging Threats
Now, let’s talk about your private keys and wallets. Your private key, that’s like the secret code to your crypto vault. If someone gets it, they get all your crypto. Scary, huh? You need to protect it like a treasure.
It’s not just hackers we’re worried about. There’s this thing called the “51% attack.” Some sneaky folks might try to take over half the blockchain network. If they do, they could twist things around, make fake transactions even. We call that double-spending, and it’s bad news.
There are also smart contract slip-ups to watch out for. These contracts, they’re like deals set in digital stone. But if there’s a bug, hackers could worm their way in and snatch your crypto. And don’t get me started on quantum computers. They could break codes like snapping twigs in the future.
So, what should you do? Keep your private keys offline if you can, like on a piece of paper or a hard drive that’s not hooked to the net. This way, hackers can’t just swipe it online. Get yourself a good hardware wallet too. It’s harder for hackers to crack.
Also, double-check everything. Before you send your crypto, make sure the address is right. A tiny mistake could send your crypto into a black hole. Oh, and keep an eye out for phishing. That’s when scammers trick you into giving up your keys. They’re sneaky, so you be even sneakier by being cautious.
To sum it up, stay sharp. Keep your software tight, your private keys secret, and your wallet secure. Use your smarts to steer clear of scams. Remember, the world of crypto is wild, but you can tame it with the right moves.
Navigating Compliance and Security Threat Intelligence
Blockchain Compliance and Cryptographic Challenges
Getting compliance right in blockchain is tough. The rules can be a maze. And crypto’s backbone, cryptography, poses big challenges. As regulations get tighter, we need to stay ahead to make sure blockchain folks don’t fall into legal traps.
Let’s talk about crypto network attacks. The big one is the 51% attack. It happens when a group controls half of a network’s power. They can block new transactions and even reverse completed ones. Think of it like a group taking over a town’s traffic flow. It’s scary but real.
Decentralization is the heart of blockchain, but it’s got loopholes. Some end up with too much say over the network. That can lead to bad stuff, like double-spending or denying others access. It’s like if the few in charge of a school fair decide what games everyone can play. Not fair, right?
A Sybil attack is another sneaky move. It’s like a person faking identities to vote many times in a contest. It hurts the network’s trust and can mess up how decisions are made. Keeping these attacks away is big for keeping blockchains strong and trusted.
Now, quantum computing is a brainy topic. But here’s the lowdown: these super machines might break our crypto codes someday. If that happens, our private keys aren’t so private anymore. It’s like suddenly finding out your secret hideout is on live TV.
Together, we’re pushing hard to seal those gaps. We’re cooking up smarter security measures to keep your digital dollars safe. Imagine a world where your coins are snug as a bug, no matter the cyber storm outside.
Leveraging Threat Intelligence to Counter Zero-Day Exploits and Ransomware
Zero-day exploits are hackers’ golden tickets. They find holes in the code before anyone else. It’s like a burglar finding your hidden house key. They slip in, take what they want, and leave no trace. We work to catch these flaws early, slamming the door shut before the bad guys get in.
Ransomware is a mean game where hackers lock up your files and ask for cash. Think of it as someone taking your favorite toy and not giving it back until you pay up. Crypto wallets are tasty targets for these cyber crooks.
Getting ahead of these threats calls for slick threat intelligence. We’ve got to be like detectives, finding clues and solving puzzles before they become disasters. We gather the latest scoop on how hackers think and act, so we can be one step ahead.
We even look out for the sneaky signs of a blockchain phishing scam. You’ve got to watch for fishy emails that try to trick you into giving up secrets. It’s like a con artist asking for your house keys to ‘check your security.’ Don’t buy it!
To boost our battle against these sneaky attacks, we always scan for software bugs in blockchain code. Fixing these bugs quickly is key to keeping our blockchains safe.
We’ve got to keep our eyes open and sharpen our tools. The mission is to build a blockchain world that’s safe, strong, and sticks to the rules. It’s all about putting up the good fight, so your investments stay as safe as a treasure chest locked up tight.
In this post, we looked deep into what can go wrong in the blockchain world. We saw how quantum computing can shake things up and how crypto networks face attacks that change all the time. Smart contracts and consensus protocols aren’t bulletproof either. They have points where they can break, like with 51% and Sybil attacks.
To keep your digital money safe, you need tough security at every step. This means guarding the end points and protecting your private keys and crypto wallets from new dangers. And with rules and smart threat knowledge, you can stand up to zero-day exploits and ransomware.
Let’s keep our heads on straight and our assets safer. By knowing the threats and how to fight them, we’re set up to win against the risks out there. Stay sharp, stay secure, and keep learning. Our digital world is worth protecting.
Q&A :
What are the emerging threats to blockchain security?
With advancements in technology comes evolving challenges in securing blockchain systems. Emerging threats include quantum computing, which can potentially break cryptographic algorithms, and smart contract vulnerabilities, which can be exploited if the code is poorly written or audited. Additionally, 51% attacks, where a user or group gains majority control of the blockchain’s hash rate, continue to pose a serious risk, enabling them to double-spend coins and disrupt the network.
How can one safeguard against new vulnerabilities in blockchain?
To protect against new vulnerabilities, it is essential to implement robust security practices. These may include constantly updating and auditing smart contract code, employing multi-signature protocols, and building decentralized applications (dApps) with security in mind from the outset. Regularly conducted network stress tests and community-driven security initiatives can also help mitigate risks. Moreover, staying informed about the latest security research and updates in blockchain technology is crucial.
What role does quantum computing play in blockchain security threats?
Quantum computing possesses the potential to undermine the cryptographic foundations of current blockchain technologies. Since blockchains rely heavily on cryptography for security measures such as public and private keys, the advent of quantum computers could enable adversaries to break these cryptographic elements, compromising the integrity and security of blockchain networks. It’s a significant threat to consider, as these computers could decode cryptographic hashes and signatures much faster than conventional computers.
Are smart contracts a weak link in blockchain security?
Smart contracts can be a weak link in the blockchain ecosystem if they are not designed and implemented securely. As executable programs that automatically enforce contract terms, they are only as secure as their code. Vulnerabilities or bugs in smart contracts can be exploited by attackers to conduct unauthorized transactions or access confidential data. This makes thorough testing and regular security audits crucial for maintaining the integrity of smart contracts.
How does blockchain’s decentralized nature influence its security vulnerabilities?
Blockchain’s decentralized nature ironically both strengthens and weakens its security profile. While decentralization reduces the risk of a single point of failure, it can also introduce new vulnerabilities such as the potential for 51% attacks, or the difficulty in updating the protocol compared to centralized systems. In decentralized systems, network consensus is required for changes, which can slow down response times to emerging threats. However, it also means that attacking a blockchain system requires compromising a significant portion of the network, which should be a difficult and resource-intensive task.




RELATED POSTS
Bitcoin Charlotte and 3 Expected Growth Signals
Bitcoin Charlotte is not just...
GRVT Airdrop – The 2 Most Important Expectations
The GRVT Airdrop offers a...
What is Data Availability Blockchain? Unraveling Decentralized Access Secrets
What is data availability blockchain?...
Can Blockchain Revolutionize Voting? Unpacking Fraud Prevention Potential
Can blockchain prevent voter fraud?...
How Companies Using Blockchain Technology Are Revolutionizing Operations
Curious about how “Companies Using...
Can you short Bitcoin? – Exploring the Secret
Can you short Bitcoin? This...
Mechanics Of Blockchain Technology: How It’s Transforming Tech
Learn the Mechanics of Blockchain...
Messari Crypto: A powerful tool for investors
In the world of cryptocurrency,...
How Blockchain Works In Simple Terms: Basics For Beginners
Discover the key principles of...
How to create a Meme Coin on Pump.fun: A Simple Guide
Meme Coins are a booming...
Smart Contract Security: Top Best Practices for Foolproof Development
Discover the Best Practices for...
The Evolution of Cryptocurrency and Blockchain Technology – 7 Things to Look Forward To
Cryptocurrency and Blockchain Technology have...
HOT!!! Notcoin Accuses Bidget of Lying!
Notcoin Accuses Bidget of Lying!!!...
BlockMesh Airdrop – From Idle Bandwidth to $BMESH
BlockMesh Airdrop helps turn idle...
Comedian Airdrop – Token BAN Leads the Memecoin Trend
In the world of memecoins,...
What is the ALIENX Airdrop and How to Participate Effectively
Do you want to invest...