Category Archives: Security
Phishing Attacks in Blockchain: How to Shield Your Digital Assets
Protect your blockchain assets from phishing attacks. Implement security measures for your digital wallet and...
How to Secure Public Keys: Unbreakable Techniques for Safe Storage
Discover best practices for securing public keys, ensuring encryption key storage, and managing PKI infrastructure...
What Is A Sybil Attack? Sybil Attacks Uncovered
What is a Sybil attack? Learn the nature of Sybil attacks, the role of Sybil...
Replay Attacks on Blockchain: Protecting Your Digital Assets
Protect your digital assets from replay attacks on the blockchain. Strengthen wallet defenses and implement...
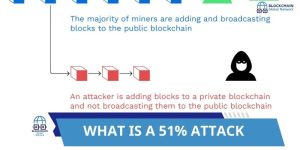
How does a 51% attack work? How Can Undermine Blockchain Security
Understand the mechanics of a 51% attack and its consequences. Learn about defense strategies and...
Unpacking Types Of Attacks On Blockchain Various
Types of attacks on blockchain - Discover the dangers of 51% attacks and double spending....
How to Secure Private Keys: Your Essential Guide to Cryptographic Safety
Learn how to secure private keys with robust security measures, encryption, multifactor authentication, and secure...
DoS Attacks on Blockchain: Protecting Your Crypto from Cyber Threats
Protect Your Blockchain Network: Learn How DoS Attacks Target and Disrupt Distributed Systems. Strengthen Defense...
What is a 51% attack? How a Blockchain Takeover Threatens Your Crypto
What is a 51% attack? Understanding the vulnerabilities of blockchain security, the consequences of majority...
Security of Proof of Work: Is Your Cryptocurrency Safe?
Security of Proof of Work (PoW): Understanding vulnerabilities, attack prevention, and network security in blockchain...