You’ve heard of hackers and viruses, but what is a Sybil attack? It’s sneaky – one user forms many fake IDs to fool a network, like a trickster in a digital mask. Picture this: Sybil nodes act as a crowd that nods along, manipulating trust and breaking the system’s backbone. It’s a digital con artist at its finest, where numbers game can become a network’s crisis. And yeah, they’re after decentralized systems like blockchain, playing peer-to-peer networks like a fiddle. Stick with me, and let’s unmask this cyber riddle. We’ll slice through the tech talk and get real about keeping your digital life sealed.
Understanding the Nature of Sybil Attacks
What Is a Sybil Attack?
Have you heard of a Sybil attack? It’s like having fake friends on a network. But these fake friends are there to hurt it. In a Sybil attack, one user makes many fake identities. They use these to gain power in the network. Think of it like cheating in a voting system by voting many times. This is a big problem in computer systems, especially when no one is in charge, like in decentralized systems. Sybil attackers create these identities to trick others and damage the system. They can spread lies, steal data, or even take over parts of the network.
To spot and stop these attacks, we need to be smart. We work on finding ways to check if users are real. We also build tools to fight back against these fake identities. By doing this, we keep networks safe and trusted. When trying to understand a Sybil attack, start by imagining one person holding many masks. Each mask lets them pretend to be a new user. In the world of computers, this can cause chaos. Now, you know that safety comes from checking who is behind each mask.
The Role of Sybil Nodes in Compromising Network Integrity
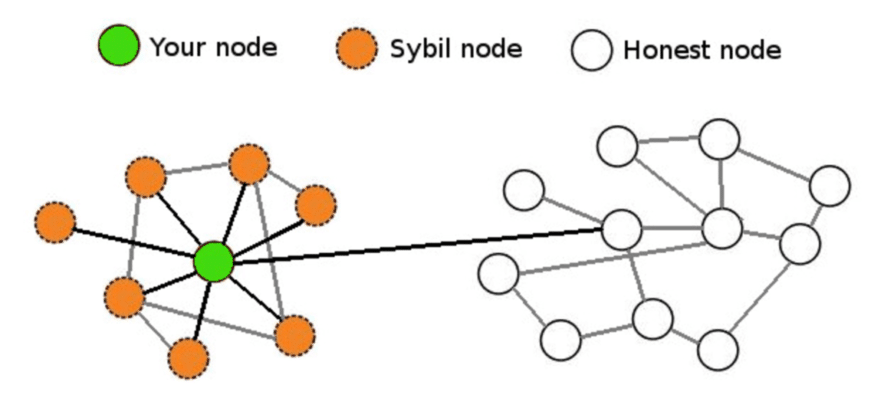
What are Sybil nodes, you ask? They are like spies hiding in a network. They are fake points in a computer network made by attackers. These spies can chat, make deals, or connect with real users. But their main goal? To trick the network and help the attacker. They can lie about who they trust or mess up the way data moves around. This breaks the trust in the network.
When too many Sybil nodes pop up, they can fool the system. This can cause honest users to work with the fakes. This trust is what lets Sybil attacks do harm. Think of a neighborhood where some houses are fake. They look real from outside, but inside there’s nothing. If we trust those houses, we might end up in trouble. It’s like that in networks too. It’s vital to find and block these fake nodes to keep our digital neighborhoods safe.
Sybil attacks mess with the health of peer-to-peer networks, decentralized systems, and even cryptocurrency. They can make it hard to know who to trust. In these systems, trust is like the glue that holds things together. If trust goes away, it can all fall apart. It’s our job to create strong defenses that keep these attacks out. This means having good checks in place to make sure every user is who they say they are.
Next, I’ll share with you how these checks work. And I’ll show you the cool tools we’re making to stop these fakes. If we stick together, we can keep our digital world secure. Let’s get smart, let’s get tough, and let’s keep our networks true.
The Vulnerabilities of Decentralized Systems
How Fake Identities Threaten Blockchain Security
Imagine a blockchain like a big safe. Now, picture a thief making copies of the key. That’s kind of what happens in a Sybil attack. Bad guys create lots of fake identities to get control.
A secure blockchain fights against fake users. But Sybil nodes are sneaky. They trick the system, acting like lots of separate users. Fake identities in blockchain are a real headache. They can mess up how decisions get made.
In peer-to-peer networks, trust is everything. Without trust, things fall apart. Sybil nodes use that trust against us. That’s why Sybil-proof protocols are so crucial. It’s like teaching the network to spot fakes.
Lots of smart people are working on this. They’re inventing cool tools to catch Sybil attackers. It’s a big deal because these bad guys want to cheat the network. They might lie, fake their address, or use tricks to look good. But really, they’re trying to break the trust that lets us all work together.
The Susceptibility of Peer-to-Peer Networks to Sybil Schemes
Peer-to-peer networks have to be super careful. If even one Sybil node gets in, it can cause big problems. It could trick the network and steal stuff. Things like your data or even your money in cryptocurrency.
To keep networks safe, there has to be a way to check who’s real. Like, really tight rules on who can join. This is what we call digital identity verification. It checks that each person in the network is who they say they are. If they can’t prove it, they can’t cause trouble.
Preventing these attacks isn’t easy. Networks need smart defenses. They need to think ahead, plan, and even learn on their own. Things like machine learning can help make the network smarter. It can learn about the bad stuff and how to stop it before it happens.
When you’re dealing with stuff on the internet, Sybil attack challenges are everywhere. You might not see them, but they’re lurking. It’s why people like me are always finding new ways to fight back. We have to keep our digital world safe, just like the real one. We can’t let the fakes win.
Remember, Sybil attacks can even hit your smart devices at home. They’re tougher to stop than you might think. So, it’s key that everyone helps to keep an eye out. We need everyone’s smarts to create a web that’s safe for all of us.
Defending Against Digital Deception
Strategies for Sybil Attack Prevention
A Sybil attack is when one user pretends to be many. In networks, this can cause big trouble. In peer-to-peer networks and decentralized systems, trust is key. Yet, Sybil attackers break this trust using fake identities. They’re like wolves in sheep’s clothing, but in digital form. To guard against these, I dive deep into ethics and smart design.
Preventing Sybil attacks starts with knowing who’s who. Identity proofs stop fake accounts from messing up the system. Think of it as a bouncer at a club, checking IDs. In computer science, it’s kind of the same. We check digital IDs to keep the network safe. We often use a thing called “resource testing.” This makes sure each user is a real person. It can be like solving puzzles that only humans can.
Network security challenges keep changing. As an expert, I can tell you, there’s no one-fix solution. You’ve got to keep your guard up all the time. We learn from real-world examples to build stronger walls. And yes, we build Sybil-proof protocols. Imagine creating rules for a game that even the sneakiest player can’t cheat.
Here’s the thing—Sybil attackers want to take advantage. They use tactics like IP address spoofing. That’s like wearing a mask to hide your real face. Then they might mess with the reputation system. This gives them an unfair edge. But we’re catching up. With every move they make, we get smarter, too.
Currencies like Bitcoin face these troubles too. They rely on consensus protocols, which means everyone has to agree on the rules. If enough fake identities join, they could sway decisions the wrong way. But the good news is, we’re getting better at spotting these fakes.
In the end, Sybil attack prevention is all about staying two steps ahead. Think of it as a game of chess with the safety of our digital world at stake.
The Importance of Digital Identity Verification in Network Safety
Now, verifying digital identity is not just nice to have—it’s a need. When we talk about network safety, we’re really talking about keeping our digital world honest. Fake identities in blockchain can trick the whole system. In peer-to-peer (P2P) networks, it’s critical too. Here, everyone relies on trust.
So, how do we make sure people are who they say they are? The method? Digital identity verification. Imagine signing in with a unique key that no one else has. That’s kind of what it’s like. This step is where trust begins.
We’ve all heard of identity fraud. In Sybil attacks, it’s the main thing. Someone pretends to be many, and chaos can follow. But if we can check each person’s ID, we cut the problem at its root.
Here’s a cool fact—did you know that even the shiny world of cryptocurrencies uses this? Yep, your Bitcoin stays safer when everyone’s identity checks out. We want to stop Sybil attackers from getting even a toe in the door.
Limitations do exist, sure. But we don’t let that stop us. We keep making our defenses stronger and smarter. To keep networks safe, we work on Sybil resistance all the time. It’s a bit like keeping up with the latest fashion, but for computer safety.
It’s all about the trust. Without it, networking falls apart. I always say that a network’s strength is in its honesty. And that starts with making sure each user is real and verified. It’s the shield that guards the realms of cyberspace, you could say.
Advanced Techniques and Future Directions
Leveraging Machine Learning for Enhanced Attack Detection
Machine learning is a game-changer for finding Sybil attacks. We teach computers to spot fake users, making our networks smarter. You might wonder, “Can machines really sniff out these cyber tricksters effectively?” Yes, they can. Picture a guard dog being trained to catch a specific scent. Just like that, we use data to train computer systems. They learn to detect odd patterns that humans might miss.
By analyzing tons of data, these smart systems notice when something is off. For example, they observe how often users talk to each other or how many new friends a user adds in a short time. When things don’t add up, the system raises an alarm. This is like a school teacher who spots a new kid in class every single day. Eventually, she’ll sense something’s not right.
But it’s not just about catching the bad guys once they’re in. It’s about keeping them out to begin with. Machine learning helps by improving systems that check who enters our digital playground. This means building a strong fence that can tell the difference between a friend and a foe.
The Evolution of Sybil-Proof Protocol Design
Now, let’s talk about designing systems that resist Sybil attacks from the start. Think of it like building a fortress. We’re the architects crafting walls that keep intruders out. We work hard to create rules, or protocols, that make it tough for attackers to break in.
What are these protocols exactly? They are like special codes that have to be followed. They make sure every user is who they say they are. A big part of this is verifying identities. We use things like digital signatures, just like a secret handshake that proves it’s really you.
There’s a real focus on making these checks better. We look at how we test resources, like computer power or time spent online. This helps us confirm each user is unique. After all, two users can’t share one computer at the same time. We want to catch copies or fakes, and let only the real people in.
Also, we want to protect things that are valuable like money or important info. We do this by using something called ‘consensus protocols’ in systems like blockchain. It’s like when all your friends agree that the same person scored the winning goal. These protocols help everyone agree which transactions are legit.
We’re not just making do with what we’ve got; we’re finding new solutions. We’re like detectives inventing new ways to catch crafty criminals. The more we learn about why and how Sybil attackers do their thing, the better we can defend.
By linking hands with smart people across the world, we make our work even stronger. We all face these tricky network puzzles together. It takes a lot of teamwork, but we’re up to the challenge.
Remember the guard dog and the school teacher I mentioned before? We’re kind of like them, but for the internet. We watch over your digital playground to keep it a fun and safe place for everyone.
In this post, we’ve uncovered what a Sybil attack is and how it risks our online safety. We explored how fake identities can shake up blockchain security and peer-to-peer networks. But there’s hope! We’ve seen how smart strategies and identity checks can block these sneaky moves. We can’t stop there, though. With machine learning and new tech, we’re building even stronger shields to keep out these cyber tricks. Keep a close eye on tech updates; staying ahead is key to keeping our networks safe from these threats. Remember, being alert and informed is your best defense. Together, we’ll make sure the online world stays secure.
Q&A :
What exactly is a Sybil attack in the context of computer security?
A Sybil attack is a type of security threat on an online system where one individual tries to take over a network by creating a large number of pseudonymous identities. This allows them to exert a disproportionately large influence and potentially disrupt the network’s processes, often to gain an unfair advantage or manipulate the system in some malicious way.
How does a Sybil attack affect decentralized networks or systems?
Decentralized systems, like those found in blockchain technology or peer-to-peer networks, rely on the consensus of their participants to make decisions. In a Sybil attack, the attacker can create many false identities that appear to be separate, independent nodes or users. This can undermine the consensus mechanism, as the attacker’s multiple identities may influence decisions, transactions, or validations in a way that benefits the attacker or compromises the integrity of the system.
What are the common countermeasures against Sybil attacks?
To protect against Sybil attacks, systems often employ various authentication methods to verify the identities of users or nodes. Techniques such as requiring cryptographic proof of work, implementing robust identity verification procedures, accounting for the reputation of participants, or using a trusted central authority for user validation can help mitigate the risk.
Can Sybil attacks be completely prevented?
While it is extremely challenging to completely prevent Sybil attacks, especially in open and decentralized networks, the risk can be significantly reduced through careful system design and the implementation of sophisticated defense mechanisms. Systems can be designed to detect and isolate suspicious activity, require substantial cost or effort to create accounts, or use social graphs to identify and weed out fake identities.
Who is at risk of Sybil attacks and why should they be concerned?
Any network or community that relies on a trust-based or democratic decision-making process is susceptible to Sybil attacks. This includes cryptocurrencies, online voting systems, and peer-to-peer networks. Stakeholders in these systems should be concerned about Sybil attacks because they can compromise the trust, fairness, and security of the system, leading to financial loss, misinformation, or the failure of the network to meet its intended purpose.

RELATED POSTS
Cryptocurrency Unveiled: Unlocking the Mysteries Beyond Blockchain
How is cryptocurrency different from...
Economic Bubble in Crypto – 3 Experiences to deal with it
In the volatile cryptocurrency landscape,...
Guide to voting in Project Catalyst
Ready to help build Cardano?...
On-Chain Essentials: Unraveling the Backbone of Blockchain Technology
Dive deep into on-chain transactions,...
Blockchain Layer 1: The Foundation of Decentralized Technology and U2U Network’s Vision
Blockchain technology has revolutionized the...
On-Chain Analysis Unveiled: Unlocking the Advantages for Savvy Investors
Gain comprehensive market insights with...
BulbaSwap Airdrop: A unique investment opportunity in DeFi
BulbaSwap, a decentralized exchange (DEX)...
Major airdrop – Easy wealth with Major Tokens
Looking for a game that...
MiCA: A new regulation or a restraint on Crypto?
Starting from December 30, the...
Innovation in Blockchain Security: How Attacks Are Sparking Genius Breakthroughs
"Innovation in blockchain security due...
Dawn Airdrop – Unique Reward Mechanism and How to Participate
Dawn Airdrop stands out with...
Converting 900 MATIC to USD: Current Rates and Simple Calculations
Curious about the current value...
Trump Bitcoin reserve: A game changer for U.S. economy
The Trump Bitcoin reserve proposal...
Who founded Bitcoin? Who is the owner of bitcoin?
Who founded Bitcoin is a...
Security Challenges in Interoperable Blockchains: Navigating the Complex Web
Discover the security challenges in...
What is a honeypot in Crypto? Unveiling the Deceptive Traps!
What Is a Honeypot in...