In the wild west of crypto, your stash is only as safe as your weakest link. Think of mitigating risks of majority mining attacks like a high-tech lock on your digital treasure chest. It’s the barrier between your investment and the outlaws of the internet. Ready to safeguard your slice of the virtual gold rush? Let’s dive into the strategies to keep your coins out of the crosshairs.
Understanding Majority Mining Attacks and Their Implications
What Are 51% Attacks and How Do They Compromise Blockchain Security?
A 51% attack happens when a miner or group controls most of the network’s mining power. This lets them block new transactions or reverse completed ones, leading to “double spending.” The attacker can stop other miners from completing blocks, letting them control the blockchain.
For instance, if you’re selling goods online and accept cryptocurrency, an attacker could make a payment, receive the goods, and then reverse the transaction. There’s no way to get those goods back once this happens. This undermines trust in the blockchain, and that’s why 51% attack prevention is critical.
These attacks are a threat to the consensus algorithms security that helps all users agree on the state of the blockchain.
The Consequences of Majority Attacks on Proof of Work and Proof of Stake Systems
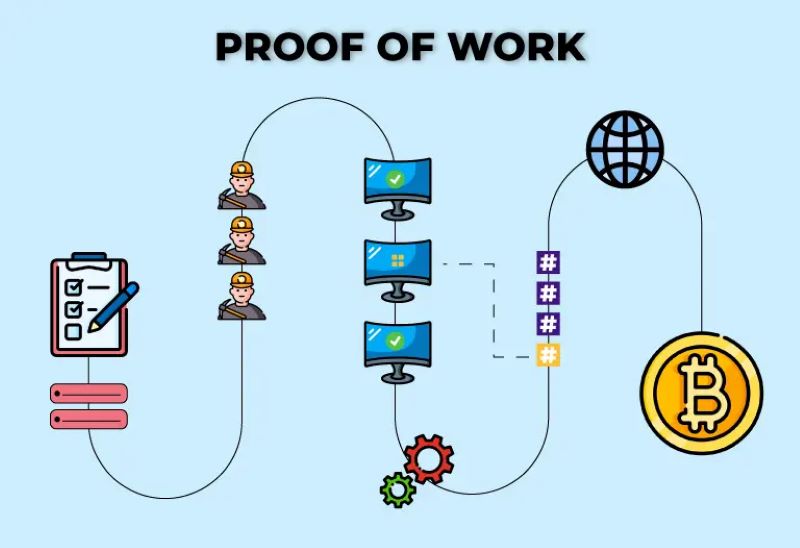
Proof of Work (PoW) and Proof of Stake (PoS) are different but both can fail due to 51% attacks. PoW networks like Bitcoin require miners to solve complex puzzles, which uses a lot of computing power, called hash power. If someone gets too much hash power, they can control the network.
Proof of Stake is different because it doesn’t need much energy. Users “stake” their coins as a way to validate transactions and create blocks. Yet, if a user owns more than half the stake, they can also control the system, including validating fraudulent transactions.
Both systems risk decentralized network safety if they allow double spending. Crypto mining security measures are there to stop this from happening. This includes watching the network hash rate. It’s crucial to keep a network where no single miner or pool has too much power.
Miner collusion defense is also key. Miners or pools might work together to get control. But fair hash power distribution is a good way to prevent that. This means spreading out the power to validate blocks evenly. It makes the network more stable and safe for everyone.
Also, protecting against Sybil attacks is essential. These happen when someone creates many fake identities to gain influence over the network. It’s one of the many reasons why the security of blockchain protocols must forever be on the cutting edge. Maintaining the blockchain’s immutability is at the core of trust in its system.
Advanced Consensus Mechanism Hardening Strategies
Enhancing Proof of Work and Proof of Stake for Increased Resistance
We face a big risk in crypto: the 51% attack. It happens when one group controls most of the mining power. They can mess up the network and double-spend coins. To stop this, we can make Proof of Work (PoW) and Proof of Stake (PoS) better. These rules are how new blocks get added to the blockchain.
For PoW, we mean tougher math problems. This means miners need more power to control the network, making attacks hard. We focus on fixing PoW flaws. This keeps the network safe and makes miner cheating unlikely.
PoS needs users to “stake” their coins for the chance to add new blocks. To protect PoS, we need to make sure one user can’t stake too much. We do this by creating rules to limit staking. This helps spread staking power fairly.
Implementing Node Diversity and Peer-to-Peer Network Fortification
Next up is node diversity. Nodes are computers that keep copies of the blockchain. We want lots of them, run by different people. This makes it hard for attackers to own the network. Node diversity helps keep our crypto safe.
We also work on peer-to-peer (P2P) network fortification. This is the system that lets nodes talk to each other. It’s like the spine of the blockchain. Strong P2P networks resist attacks and keep things like Sybil attacks—where one person acts like many—away.
In P2P, we use clever crypto math called cryptographic hash functions. These are codes that lock each block. They need to be unbreakable. We also watch the network hash rate. This is the power of all mining combined. A good watch keeps attacks at bay.
To sum it up, our safety plan is to make PoW and PoS stronger and spread out the node power. We also make sure our network talks strong together. This means good guys stay in charge, and our digital cash stays safe.
Proactive Measures in Network Monitoring and Hash Power Management
Critical Role of Network Hash Rate Monitoring in Preventing Attacks
Watching the network hash rate is key to stopping attacks. What’s a network hash rate? It’s how much crypto mining power the network has. If it’s too focused in one place, it’s a problem. Why? Because then someone could control over half of it. They could mess with things, like spending the same coin twice. This is bad.
So, we keep eyes on the hash rate. We do this to find any signs of danger early. It’s like being a lookout on a ship, scanning for threats. With good tools, we see shifts in power. And we can be ready if someone tries to take over. Our goal is to keep the network safe and trusty for everyone.
Fair Distribution of Hash Power to Curtail Miner Collusion
We need to spread out mining power, too. We call this “hash power.” When it’s in too few hands, they might work together in a bad way. This makes things less fair and less safe.
So what do we do? We make rules for how mining pools work. We want many different people to have a say in what’s going on, not just a few big ones. We also tell folks how to act right when they’re mining. This way, everyone plays by the rules, and no one cheats.
In simple talk, it’s like making sure a game is fair. No one should have all the power, and no one should change the rules to win. If we spread power out, we all win because crypto stays safe.
Let’s chat about “crypto mining security measures.” They include keeping mining software up to date and shielding miners from attacks. Think of it like this. You wear a helmet when you ride a bike. For miners, it’s about having good security to keep their work safe.
For serious safety, we also look at “consensus algorithms security.” These are the rules of how transactions get a thumbs up. We keep making these rules better so they’re harder to break. It’s like leveling up in a game. Each level makes you stronger. For crypto, it makes it tougher for attackers.
And what about “proof of work vulnerabilities”? They can be weak spots where attacks might happen. So we work hard to guard those spots. It’s kind of like patching up a hole in a fort. You don’t want anyone sneaking in.
There’s also “proof of stake protection.” This means watching who’s holding coins and making sure they help keep the network secure. Think about it as if you’re part of a team watching a treasure chest. Everyone plays a part to guard it.
We do all this because “decentralized network safety” matters. Making a network where no single person has all the power is like building a wide, sturdy base for a tower. It stands strong because the whole base holds it up.
Remember, we’re in this to make sure your crypto is safe. It’s our job to check for risks and keep the bad guys out. And we’re always on it, making things better. Keeping your crypto safe is what we do best.
Regulatory and Community-Based Approaches to Secure Cryptocurrency Mining
Enhancing Bitcoin’s Security Through Mining Pool Regulations
Mining pools need to follow clear rules. These rules help stop 51% attacks. They guard the blockchain network against those who might control it. Let me paint you a picture: Imagine many guards, each with a key to a vault. Alone, they can’t do much. But together, they keep the vault safe. That’s how well-regulated mining pools can protect Bitcoin.
By tracking hash power, we can see if a pool gets too strong. If a mining pool gets too much power, it risks the blockchain’s safety. We want to stop that. That’s why we need to keep a watchful eye on the balance of power.
Pooling miners should work like a team, not like a mob. When one miner tries to bend the rules, the others need to say, “No way!” That’s our first defense against threats. It’s simple: No one should get more than their fair share of influence.
Establishing a Miners’ Code of Conduct to Promote Ethical Standards and Transparency
A miners’ code means miners promise to play nice. They agree to respect the rules, avoid tricks, and be open about what they do. Think of it as an honor code in a school. Kids pledge not to cheat on tests. This builds trust and keeps the school fair.
In crypto, this code helps stop double spending. It also stops miner collusion – that’s when miners join forces to take control. Such teamwork could kill trust in Bitcoin. The miners’ code makes sure everyone acts right.
Transparency is key in this game. Everyone should be able to see what the miners are up to. Just like in sports, where the score is clear to all. If a miner starts playing dirty, others will spot it fast.
Let’s not forget about small players. The code protects them too. It supports a mix of big and small miners. This variety is crucial for the system’s health. It stops any single group from taking over.
Now, we can’t just trust the miners to follow these rules. In this space, trust is good but checking is better. That’s where third parties come in. They make sure miners stick to the code. It’s like having a ref in a soccer game. The ref watches every play, ensuring no foul moves.
By sticking to these plans, we stand strong against attacks. It’s like having an army ready before the battle begins. Bitcoin can then be as solid as a rock, tough to break, tough to game. This brings peace of mind to those holding or trading Bitcoin. It makes sure their digital gold stays safe.
Does this sound like a lot of work? Sure, it is. But isn’t the safety of our digital treasures worth it? By banding together, staying alert, and keeping true to the code, we build a fortress around Bitcoin, one that’s too tight and too tough for the bad guys to crack. This isn’t just smart; it’s our duty if we want to see Bitcoin thrive.
In this post, we’ve looked at how 51% attacks threaten blockchain security and the heavy toll they can take on both Proof of Work and Proof of Stake systems. We then explored ways to make these systems tougher, like beefing up network defenses and mixing up nodes. We also saw why it’s critical to keep an eye on network hash rates and spread out hash power fairly. Lastly, we talked about setting rules for mining pools and a miners’ code to keep things above board.
My final thought? Staying one step ahead is key. We must work together—coders, miners, and regulators—to shield our blockchains from attacks. It’s not just about tech fixes; it’s about our attitude too. Let’s commit to security and fair play to protect the crypto world we all rely on.
Q&A :
What are the primary risks associated with majority mining attacks in blockchain?
Majority mining attacks, also known as 51% attacks, pose significant risks to blockchain networks. Such attacks occur when a single entity or group controls more than 50% of the network’s mining power, allowing them to manipulate the blockchain by double spending coins, preventing transactions, or even reversing confirmed transactions. This undermines the trust in the network’s security and can lead to a loss of value for the cryptocurrency involved.
How can blockchain networks mitigate the risks of majority mining attacks?
To mitigate the risk of majority mining attacks, blockchain networks implement a variety of strategies. These can include employing more robust consensus mechanisms like Proof-of-Stake (PoS) or Delegated Proof-of-Stake (DPoS), which do not depend solely on mining power. Networks may also increase the number of confirmations required for a transaction, which makes it more difficult for an attacker to reverse it. Regularly updating and monitoring network security can also help to fend off potential attacks.
What measures can individual users take to protect themselves from the effects of a majority mining attack?
Individual users can take several precautions to protect themselves from the fallout of a majority mining attack. One is to wait for more confirmations on their transactions, especially when dealing with large amounts. Additionally, users should keep abreast of the security measures in place on the blockchain they are using and choose cryptocurrencies that have robust security protocols to reduce the risk of such attacks.
Can majority mining attacks be easily detected on blockchain networks?
While majority mining attacks can sometimes be detected by sharp changes in mining power or observing the reorganization of blocks, they may not always be evident immediately. Blockchain networks and users must remain vigilant for signs of unusual activity. Swift detection is crucial for enabling the network to respond and take measures to prevent the attacker from causing further damage.
What long-term solutions are being explored to prevent majority mining attacks?
In the long run, blockchain communities are exploring several innovative solutions to prevent majority mining attacks. These include creating decentralized mining pools to prevent concentration of power, adjusting the difficulty of puzzles in Proof-of-Work (PoW) systems dynamically, and evolving toward alternative consensus mechanisms that do not incentivize control of a majority of the network’s hash rate. Researchers are also working on cryptographic methods like Verifiable Delay Functions to enhance network security against such attacks.


RELATED POSTS
Challenges of Using Decentralized Learning Platforms: Is Blockchain the Solution?
Exploring the Challenges of Decentralized...
Custodial vs Non-Custodial Wallets: Which Secures Your Crypto Best?
Custodial vs Non-Custodial Wallets: Understanding...
Future of On-Chain Code Audits: Revolutionizing Collaborative Cybersecurity
Enhance blockchain security with on-chain...
What is the trading range of Kaspa standard deviation?
Are you interested in Kaspa...
Future Trends in Blockchain Security: Staying Ahead of Threats
Future trends in blockchain security:...
Advantages of Blockchain Transparency: Unveiling the Trust Revolution
Unlock the Advantages of Blockchain...
Blockchain Technology Applications – 3 Key Highlights in the economy
Blockchain Technology Applications are increasingly...
Revolutionizing the Classroom: How Blockchain Will Transform Education
Enhance education with blockchain! Strengthen...
Towns Airdrop – Expert Experience in Mining
To optimize benefits from the...
A Night of Luxury – DePIN Alliance Yacht Party
The Depin Alliance Yacht Party...
Mapping Opportunities with Funding Rate Heatmap
In the fast-paced trading world,...
Pebonk Kombat – The next frontier in gaming and crypto
Pebonk Kombat is revolutionizing gaming...
When was Blockchain Technology invented? A journey through its origins
Ever wondered, “When was blockchain...
Cryptocurrency Ro Khanna and the future of regulation
Discover how cryptocurrency ro khanna...
limitations of traditional systems in transparency: Unveiling the Gap
Limited transparency in old systems...
Unveiling the Future: Benefits of blockchain transparency
Enhance trust & transparency with...